While solving CTF or bug bounty challenges, sometimes you need to find out the IP address of the machine because that machine is not logged in at that time. We realize that some people who like to break stuff haven’t had experience in building stuff.
No matter how good our skills are, we need to find systems that we can attack. This is accomplished by probing the network and looking for a response.
One of the most popular tool to do this is the excellent open source tool netdiscover.
[#1] With Netdiscover –
You can find netdiscover by going to Kali Linux machine, then Information Gathering, then Route Analysis, about midway down the long list of discovery tools. When you click on netdiscover, it opens a screen which displays some basic help. Netdiscover is a relatively simple tool, so there are not a lot of options.
To discover the IP’s on an internal network, we will usually want to scan a range of IP addresses. In netdiscover, we can use the -r switch (for range) and then in CIDR notation provide it the network range we want it to scan.
In the command below, we are asking netdiscover to find all the live hosts with IP addresses between 192.168.73.1 to 192.168.73.255. We do this by typing;
Command: netdiscover -P -i eth0 -r 192.168.73.0/24
[#2] With Nmap Live Scanning –
Another popular tool which is nmap can also be used to find out the live hosts within a network. You can download then nmap from www.
nmap.org or you can use any number of toolkit distributions for the tool.
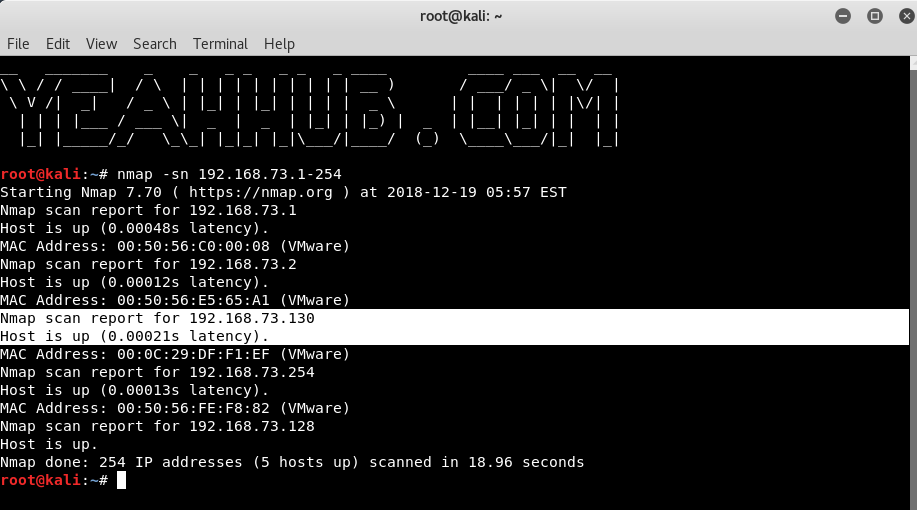
When you run the below command, nmap tries to ping the given IP address range (192.168.73.1 to 192.168.73.254) to check if the hosts are alive. If ping fails it tries to send syn packets to port 80 (SYN scan). This is not 100% reliable because modern host based firewalls block ping and port 80. Windows firewall blocks ping by default.
The hosts you have on the network are blocking ping and the port 80 is not accepting connections. Hence nmap assumes that the host is not up.
Command: nmap -sn 192.168.73.1-254
[#3] With Nmap Port Scanning –
Nmap is compatible with every major operating system including Mac OS, Windows, and Linux. We’re going to focus on using nmap to find and list all hosts on a network, and we’re assuming you already have nmap on your Kali Linux machine.
To find active hosts within a network, type the following command in your terminal:
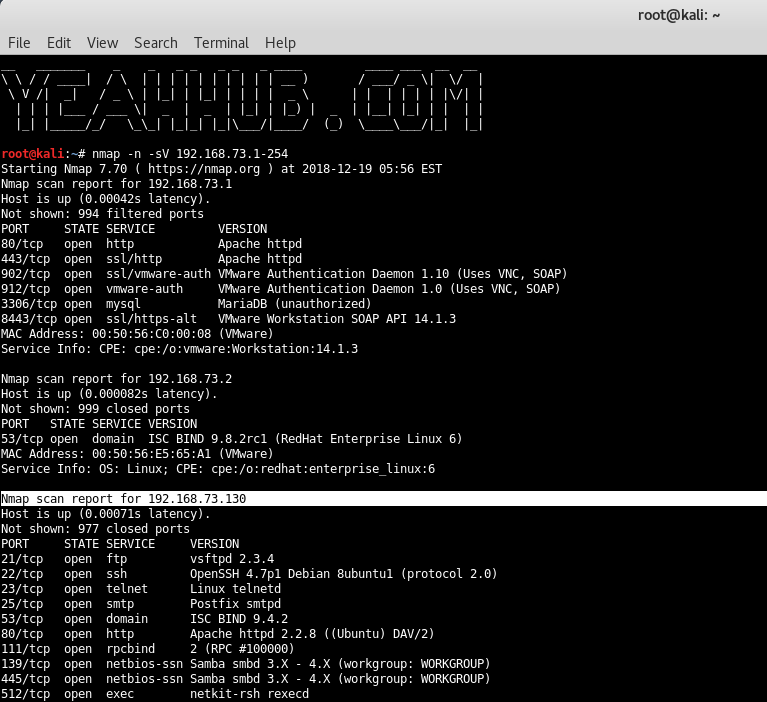
Command: nmap -n -sV 192.168.73.1-254
This is the easiest but slowest method since you’re scanning every open port on your network. Intentionally vulnerable VMs will generally have more open ports than your own attack or desktop machines.
Also Read: Top 30 Basic NMAP Commands For Beginners
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times