
As we all knows that, Shodan is one of the most popular and dangerous search engine which gives you all information from the banners and pulls from web-enabled devices like routers/switches/traffic-lights/scada/cameras etc.
There are many ways to find web cams on Shodan. Usually, using the name of the manufacturer of the webcam is a good start. Remember, Shodan indexes the information in the banner, not the content.
Today we’ll show you that, how you can find the vulnerable webcams with the help of Shodan and Metasploit Framework. To start Metasploit Framework, type “msfconsole” from your terminal.
Type “search shodan” to view all the available modules/exploits related to shodan search engine.

From all above results, just type “use auxiliary/gather/shodan_search”
This module uses the Shodan API to search Shodan. Output from the module is displayed to the screen and can be saved to a file or the MSF database. Type “show options” for all required options related to above module.
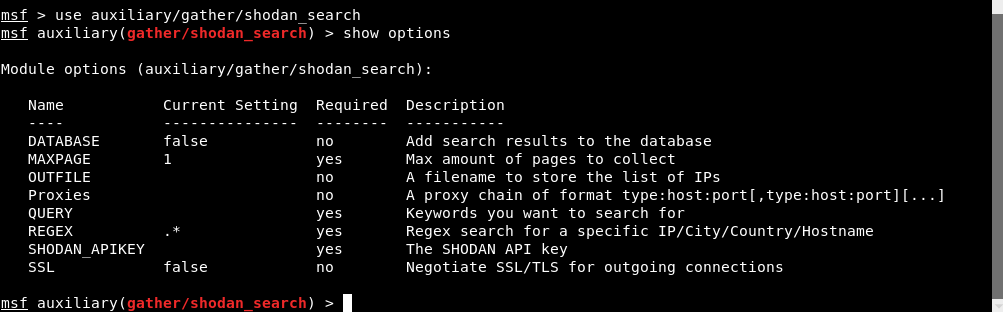
Please see the Shodan site for more information regarding API Key.

To set the Shodan Key, type “set SHODAN_APIKEY <Your key here>” and also you need to set the Query which you want to search.
In our case, we’re gonna demonstrating the vulnerable Webcams, so type “set QUERY webcamxp” and then execute the module by typing either run or exploit from the msf console.

As soon as, you run the module, you’ll get all the results which shows all vulnerable open web cameras hosted at different locations.

Here is one of the camera hosted at some roof building corner.

Although some of these webcams are unprotected, many of them will require authentication. The first step is to try the default username and password. We’ve compiled a short list of the default username and passwords of some of the most widely used webcams below.
- ACTi: admin/123456 or Admin/123456
- Axis (traditional): root/pass,
- Axis (new): requires password creation during first login
- Cisco: No default password, requires creation during first login
- Grandstream: admin/admin
- IQinVision: root/system
- Mobotix: admin/meinsm
- Panasonic: admin/12345
- Samsung Electronics: root/root or admin/4321
- Samsung Techwin (old): admin/1111111
- Samsung Techwin (new): admin/4321
- Sony: admin/admin
- TRENDnet: admin/admin
- Toshiba: root/ikwd
- Vivotek: root/<blank>
- WebcamXP: admin/ <blank>
There is no guarantee that these will work, but many inattentive and lazy administrators and individuals simply leave the default settings, and in those cases, these username and passwords will give you access to confidential and private webcams around the world!
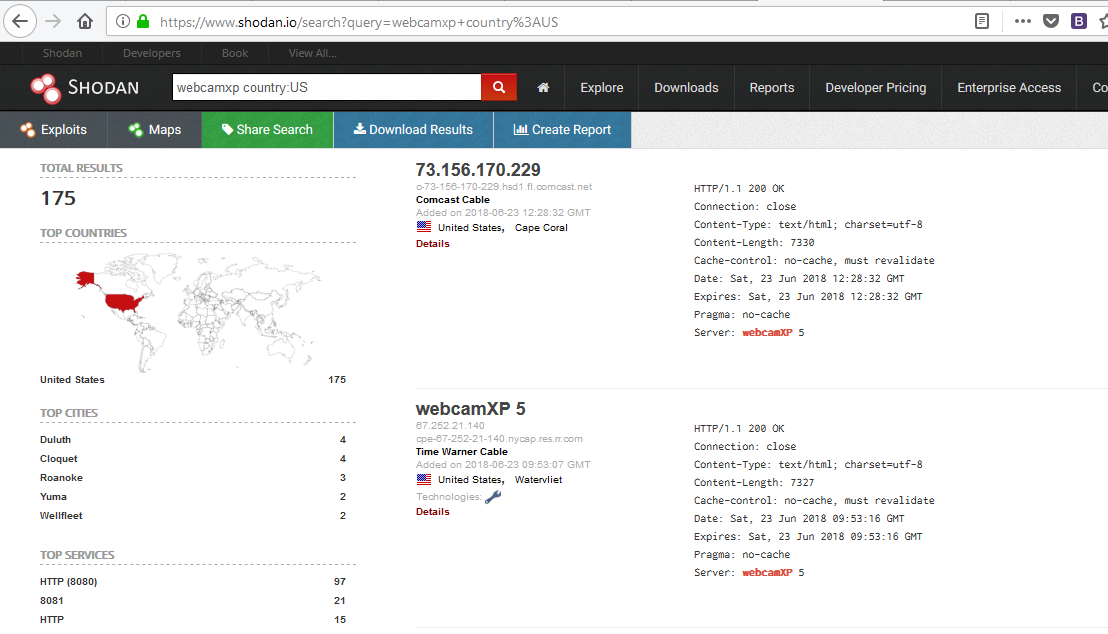
You can do the same through web portal too, for example if you want to search the webcams of only US country, then the search query is “webcamxp country:US” which will show all the results of United States country as shown below.
To be even more specific, we can narrow our search down to an individual city. Let’s see what we can find in Mexico. We can find those webcams by typing “webcamxp city:Mexico”

Shodan even enables us to be very specific in searching for web-enabled devices. In some cases, we can specify the longitude and latitude of the devices we want to find.
In this case, we will be looking for WebcamXP cameras at the longitude and latitude (19.4357,-99.1439) of the city of Mexico. When we search, we get a list of every WebcamXP at those coordinates on the globe.

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








