
SQL injection occurs when an application processes user-provided data to create an SQL statement without first validating the input and then submits the statement to a database server for execution. When successfully exploited, SQL injection can give an attacker the means to access back-end database content, remotely execute system commands and in some circumstances, take control of the server that is hosting the database.
The specific impact depends on where the error is in the code, how easy it is to exploit the error and what access the application has to the database. Theoretically, SQL injection can occur in any type of application, but it is most commonly associated with web applications because they are most often hacked.
Testing procedure
Replace the value of each parameter with a single quote and an SQL keyword, such as WHERE. Test each parameter individually. When testing parameters, leave all of the other parameters unchanged with valid data as their arguments.
The detection of SQL injection attacks has primarily been accomplished through pattern matching techniques against signatures and keywords known to be malicious. Until recently, this technique has been successful. Now attackers are hiding their malicious intent in a variety of ways to escape detection.
Today we’ll learn one more scanning tool which is a kind of SQL Injection vulnerability scanner just like SQLMAP which is the most popular tool till date. viSQL is the SQL Injection vulnerability scanner which not only scans the target URL but also scans the whole server with the help of crawling and reverse IP domain check feature.
You can easily scan the SQL vulnerability on the target URL itself and all other sites on same server.
Installation of viSQL in Kali Linux –
To install viSQL, please type “git clone https://github.com/blackvkng/viSQL.git” in your Kali Linux terminal.

The above command will automatically creates a folder named “viSQL” in same directory where you are running the command. To list out all the files, type “cd viSQL && ls” in your terminal.
Second method for installation is to download the installer.py file with the help of wget and run the installer.py with the help of python command.
Command: wget https://raw.githubusercontent.com/blackvkng/viSQL/master/installer.py
Command: sudo python2 installer.py

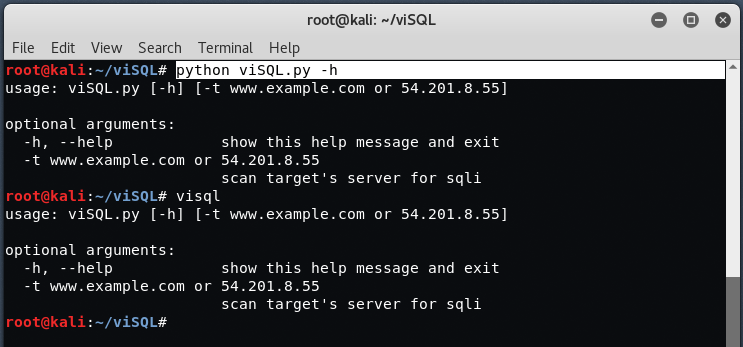
After that, to run viSQL, just type “python viSQL.py -h” which shows the help menu of viSQL tool.
To scan the site using viSQL, type “python viSQL.py -t www.example.com”
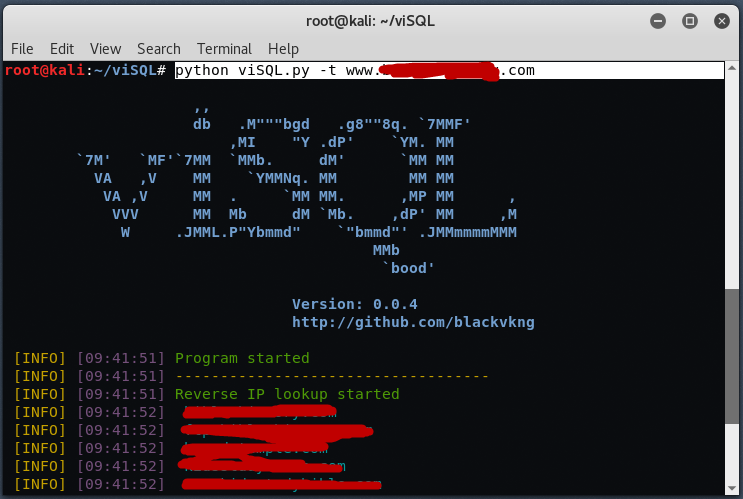
Now take a time, to let viSQL doing its job. viSQL first will doing Reverse IP Lookup to enumerate the list domain which is on this target IP, then crawling each site to find SQL injection vulnerable. If viSQL found potential SQL injection on target then it will display the SQL Injection vulnerable link in front of you.
Here you can see that, viSQL started the crawling against the target website and found so many sites which may be vulnerable to SQL Injection vulnerability.

After the completion of crawling, viSQL starts the SQLi scan feature which lists all the SQL vulnerable URLs just like below.

Now collect that link, and then start doing SQL injection manually through browser or automate it using your desirable tool just like SQLMAP or HAVIJ.
SQLMAP is for Linux based users and HAVIJ is for Windows based users.
Secure SQL coding for your web applications
You should follow some rules for preventing SQL injection attacks. Limit the rights of database users. Successful SQL injection attacks are based on database users credentials. While limiting privileges may not prevent SQL injection attacks, you can make attacks more difficult to implement. Don’t give user access to all system-stored procedures if your users need to access only a few user-defined procedures.
You may also like:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








