
The Metasploitable machines are those vulnerable machines, designed by Rapid7 Company for training offensive security skills and testing exploits.
To install Metasploitable3 on windows is not easy as Metasploitable2 installation, here you need to craft the virtual image itself with the help of vagrant and Packer tools which generally used to create virtual development environments.
Tools Required:
- Vagrant – https://www.vagrantup.com/downloads.html (Size: 196MB)
- Virtual Box – https://www.virtualbox.org/wiki/Downloads (Size: 142MB)
- Vagrant Reload Plugin – https://github.com/aidanns/vagrant-reload (Size: 5KB)
- Packer – https://www.packer.io/downloads.html (Size: 17MB)
- Metasploitable3 – https://github.com/rapid7/metasploitable3/ (Size: 113MB)
For Metasploitable3 File, either you can download the zip file via Git Utility or you can directly download the Zip file from Github Repository.
So, here we’re ready with everything to install Metasploitable3.

Install prerequisite softwares –
- Step 1. In very first step, you need to install two tools which are very straight forward i.e. VirtualBox and Vagrant. The latest version of VirtualBox is 5.2.6 (As per dated 25th Feb 2018).
Note: Make sure that you must restart your machine after the installation of Vagrant.
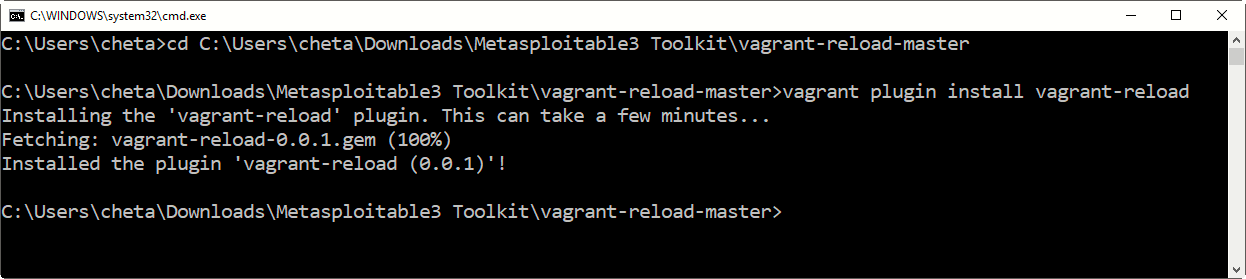
- Step 2. In second step, you need to install the Vagrant Reload Plugin by typing the following command in your command prompt windows.
Command: vagrant plugin install vagrant-reload
Note: Extract the vagrant-reload-master.zip file into a folder and then run the command by changing into that directory.
- Step 3. In last step, you need to install the Packer tool and unpack/unzip into same Metasploitable3 Directory.
Note: Storing the Packer binary in the Metasploitable3 directory allows us to easily execute it to setup the VM without setting up system variables or using full paths to the binary.
Tweaking Config File –
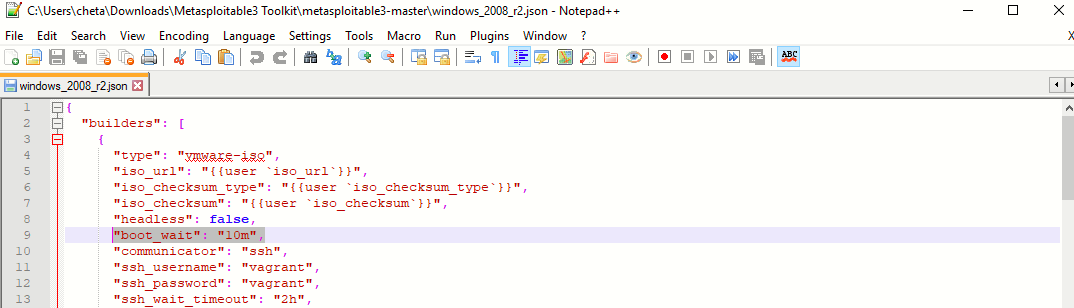
Well generally if you get any error related to “waiting for ssh..” something then you need to tweak your config file and change the boot wait time to 10m from 2m.
To change this setting, open windows_2008_r2.json file in any text editor and change the following line:
“boot_wait”: “10m”,
Creating Metasploitable3 VM –
As you’ve already installed all the required tools and placed the packer.exe file into respective Metasploitable3 directory, now its time to run the following command to build the ISO file:
packer build windows_2008_r2.json
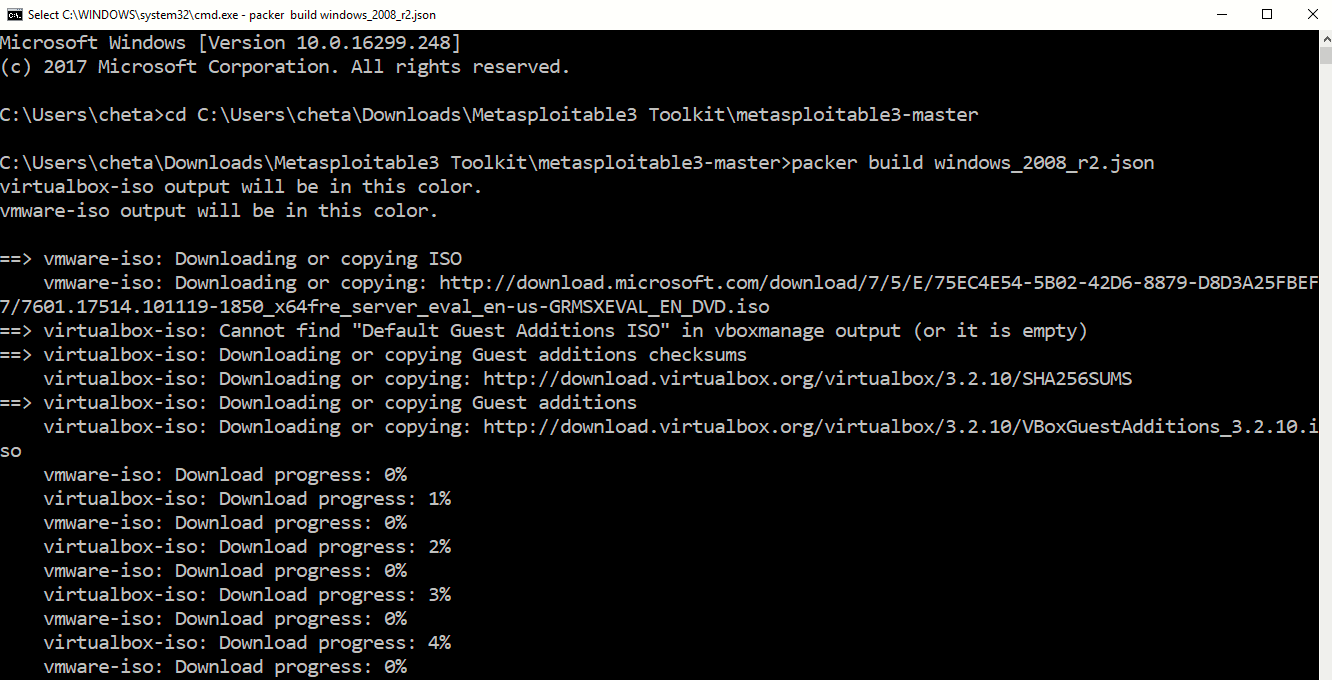
Note: The above command will take some time because it will first download the evaluation copy of Windows 2008. It also depends upon the speed of your Internet connection and your host machine configuration.
Once completed, go to same location where you’ve downloaded Metasploitable3 and confirm the windows_2008_r2_virtualbox.box file with a size just over 3GB.
If the size is small, it didn’t download correctly.
We now have the box file, but need to configure the virtual machine. This is where Vagrant comes in.
Vagrant will load all the software onto the virtual machine. Still at the metasploitable3 directory in powershell, type the following command which hardly takes less than 5 minutes to finish it:
vagrant box add windows_2008_r2_virtualbox.box –name=metasploitable3
Finally we have to run the one more command to have Vagrant execute the scripts that install the vulnerable software on the Windows server 2008 virtual machine. Run the following command and expect to wait another 15-30 minutes until completion:
vagrant up
This will cause Vagrant to kick in and run all scripts to make the machine vulnerable and fully configure the VM. When this process is complete your Metasploitable3 machine is ready to exploit!
The default username for the virtual machine is “vagrant” with password “vagrant“.
You may also like:- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times









Thanks for your sharing, do you have ova file?
I follow up your step and try to install metasploitable3 on windows 10, but i can’t success install that.
Ok We’ll share OVA file with you soon..
Another thing is When I download the Master repository I dont see “windows_2008_r2.json” file. All I see is build_win2008.ps1. Thanks
I need a vm-file for vmware.