
The information security environment has changed vastly over the years. Now, in spite of having security policies, compliance, and infrastructure security elements such as firewalls, IDS/IPS, proxies, and honey pots deployed inside every organization, we hear news about how hackers compromise secured facilities of the government or of
private organizations because of the human element involved in each activity.
Typically, employees are not aware of the tricks and techniques used by social engineers in which they can be used as mediators to gain valuable information such as credit card details or corporate secrets. The security of the entire organization can be at stake if an employee visits a malicious website, answers a social engineer’s phone call, or clicks on the malicious link that he/she received in their personal or company e-mail ID.
Having the best laptop for Kali Linux can help you make best use of this operating system.
Today we’ll show you a method through which you can easily send a fake email with one of the most popular tool called as SET (Social Engineering Toolkit).
The Social-Engineering Toolkit (SET) is a product of TrustedSec. SET is a Python-driven suite of custom tools created by David Kennedy (ReL1K) and the SET development team, comprising of JR DePre (pr1me), Joey Furr (j0fer), and Thomas Werth.
SET is a menu-driven attack system that mainly concentrates on attacking the human element of security. With a wide variety of attacks available, this toolkit is an absolute must-have for penetration testing.
SET comes preinstalled in Kali Linux. You can simply invoke it through the command line using the command “setoolkit“.
Once the user clicks on the SET toolkit, it will open with the options shown in the following screenshot:

Select 1) Social-Engineering Attacks to receive a listing of possible attacks that can be performed.
You can select the attacks that you want to perform from a menu that appears as follows:
- 1 Spear-Phishing Attack Vectors
- 2 Website Attack Vectors
- 3 Infectious Media Generator
- 4 Create a Payload and Listener
- 5 Mass Mailer Attack
- 6 Arduino-Based Attack Vector
- 7 Wireless Access Point Attack Vector
- 8 QRCode Generator Attack Vector
- 9 Powershell Attack Vectors
- 10 SMS Spoofing Attack Vector
- 11 Third Party Modules
- 99 Return back to the main menu
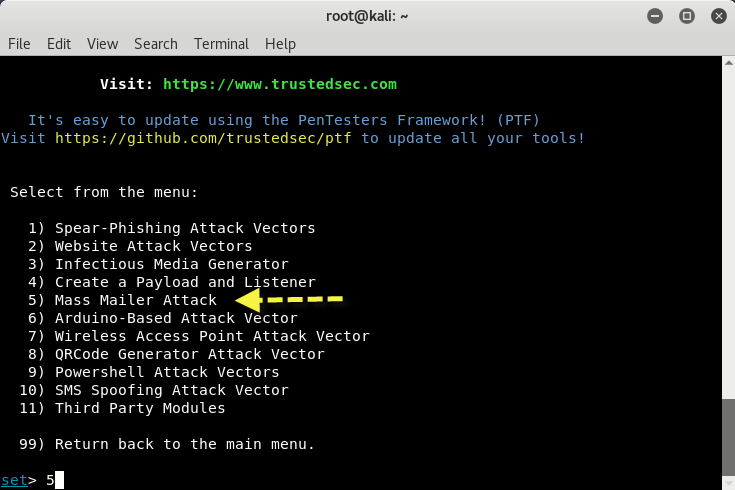
We will start with the Mass Mailer Attack. Enter 5 to move to the next menu.
For this example, on the list, we will take a look at the first option, E-Mail Attack Single Email Address.

Now further you need to fill all the following details as shown below:
- Send email to:
- From address:
- The FROM Name the user will see:
- Username for open-relay:
- Password for open-relay:
- SMTP email server address:
- Port number for the SMTP server:
- Flag this message/s as high priority?:
- Do you want to attach a file:
- Do you want to attach an inline file:
- Email Subject:
- Send the message as html or plain:
- Enter the body of the message, type END when finished:
Here you just need an open relay SMTP server which you can easily get it through smtp2go.com by creating a free account whose SMTP server address will be “mail.smtp2go.com“and port will be “2525“.

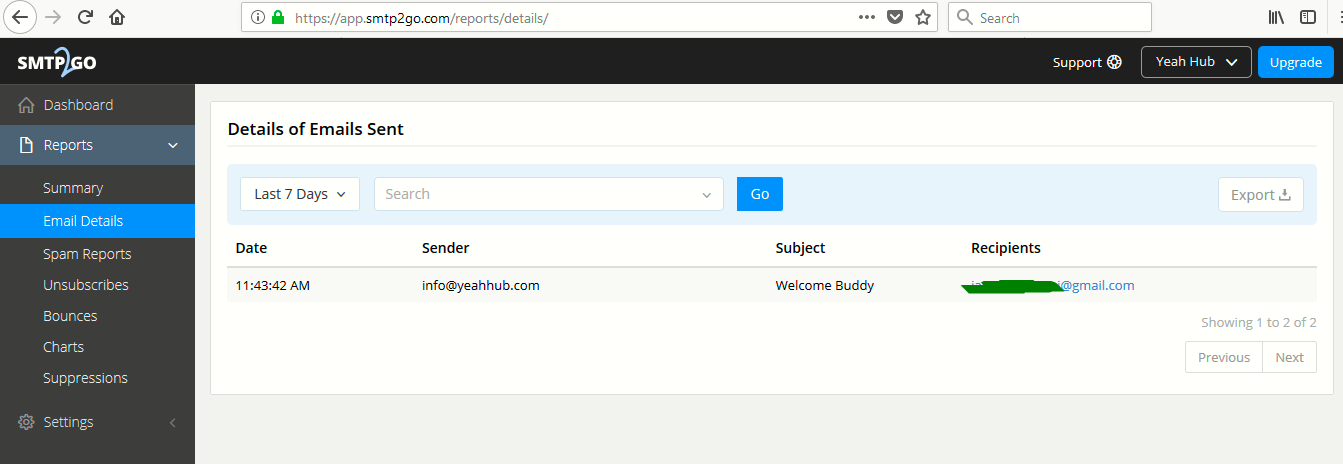
This is the output of the fake email which we sent from info@yeahhub.com via smtp2go.com open relay server.

In SMTP2GO.com App Dashboard, you can even manage all the records and can see all the information about the fake emails sent from your account as shown below:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times









Hello sir when i am trying mass mailer attack, i am not getting option for open relay to enter smtp2go settings