
SSL Kill is a forced man-in-the-middle transparent proxy that modifies HTTP requests and responses in order to avoid SSL and HSTS, to achieve that, it use a two-way ARP spoofing plus a forced DNS resolver that redirects all name server queries to the attacker IP Address.
This tool is only for information security researchers and should not be used for criminal acts.
The latest version of SSL Kill is v1.2
Installation and Usage of SSL KILL –
You can easily download the sslkill package from Github repository but before to install sslkill, we need to install some dependencies which are build-essential, python-dev and libnetfilter-queue-dev
To install these dependencies, just type
Command: apt-get install build-essential python-dev libnetfilter-queue-dev

Now we need to install sslkill package, which we can easily download it from Github via git clone command.
Command: git clone https://github.com/m4n3dw0lf/sslkill

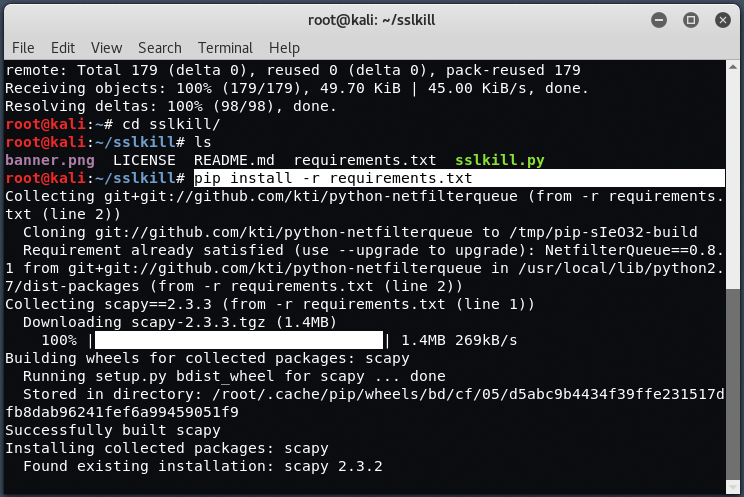
Now install all further dependencies which you can easily found in requirements.txt file and to install these dependencies just type “pip install -r requirements.txt” in your terminal.
Change the permissions of sslkill.py file with the help of chmod command and then execute “./sslkill.py” in same terminal.
Command: chmod +x sslkill.py

Now run “./sslkill.py -i eth0 -t <Target IP> -g <Gateway IP>”

Here you can see, -i stands for eth0, -t stands for Target host, and -g stands for gateway address which you can easily find by typing the command “route -n“.
Now when your target/victim opens any website based on HTTPS, all the requests will automatically be spoofed and sniffed as shown below:

- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times









everything installed fine
no errors
followed the above tutorial to the letter
the console is blank after ‘serving proxy on port 8080’
???????
I also receive an error I think you may need a different wifi adapter