
Hello geeks, today we’ll show you some basic SQL Injection techniques with the help of Python and SQLMap. SQL injection is one of the most critical vulnerabilities till now and is still included…
Read more
The Tor Project just announced the launch of a public bug bounty program where you can easily earn the money in between $2,000 and $4,000 for high severity flaws. The Tor’s Bug Bounty…
Read more
Equifax Inc. is a consumer credit reporting agency in the United States, considered one of the three largest American credit agencies along with Experian and TransUnion. Equifax is the oldest of the three…
Read more
Security is a state in which we ensure a proper gap between the threats and assets of an organization. We try to either move assets far away from threats or we try to…
Read more
The LaZagne project (A password recovery tool) is an open source application used to retrieve lots of passwords stored on a local computer. Each software stores its passwords using different techniques (plaintext, APIs, custom…
Read more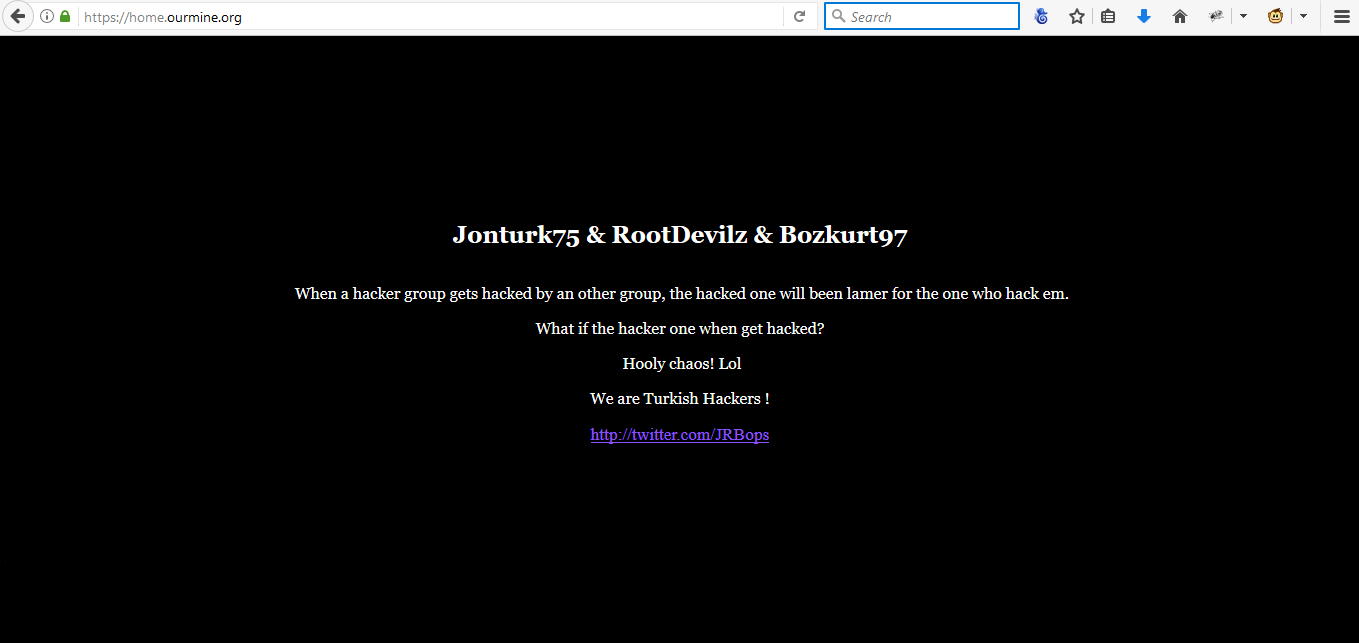
OurMine is a security hacker group based on Saudi Arabia and recently this week, they hacked WikiLeaks.org website with DNS Poisoning Attack. In a statement shared on the Twitter account of one OurMine…
Read more
Windows 10 helps you reduce the cost and complexity historically associated with managing and deploying Windows devices. With Windows as a service, you receive a continuous innovation so you are always up to…
Read more
Good password practices are critical for the following reasons: The most common form of attack on a corporate system is password guessing. On most systems, most untrusted services are protected primarily by passwords…
Read more
Ethereum is the one of the 2nd most popular digital currency after Bitcoin. As per latest stats ref. 1st Sept 2017, the value of 1 BTC and 1 ETH is: 1 BTC =…
Read more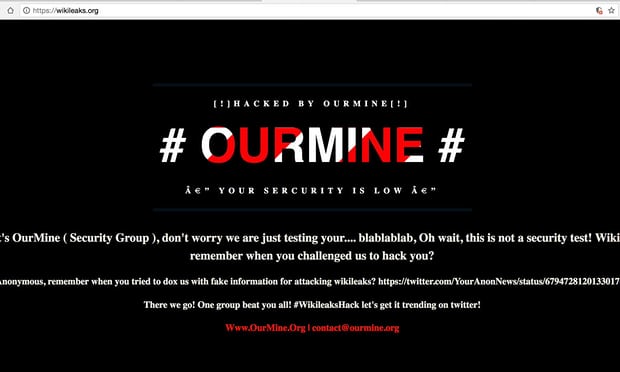
Another defacement attack just happened and this time wikileaks.org website has been hacked by OurMine Hacker which is a Saudi Arabian Hacking group who hacked so many websites last year. The group appears…
Read more