The Yuki Chan is an Automated Penetration Testing tool through which you can easily audit any website and gather all possible information like website enumeration, ssl security auditing etc. Features – Fully Automated…
Read more
The idea behind a MAC flooding attack is to send a huge amount of ARP replies to a switch, thereby overloading the cam table of the switch. Once the switch overloads, it goes…
Read more
Wireless networks were first introduced in 1991. The wireless networking is an invention that makes it possible to transfer data packets over standard network protocols: the only difference is that it uses radio…
Read more
Kali Linux 2017.2 was released on September 20, 2017. This release is a roll-up of all updates and fixes since our 2017.1 release in April. More than a dozen Open Source tools present on GitHub…
Read more
Kali Linux is a Debian-based distribution with a collection of security and forensics tools. The new version of Kali Linux i.e. 2017.2 is already been out with awesome features and is available for…
Read more
CCleaner is one of the most popular tool for cleaning for your PC. It makes it easy to speed up a slow computer and keep your activity private — automatically and in the…
Read more
As you all knows, Kali Linux is one of the most popular penetration testing operating system having more than 400+ hacking tools pre-installed in it. Kali is the latest and greatest version of…
Read more
The purpose of this article is to introduce the most popular packet sniffer i.e. WIRESHARK. The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As…
Read more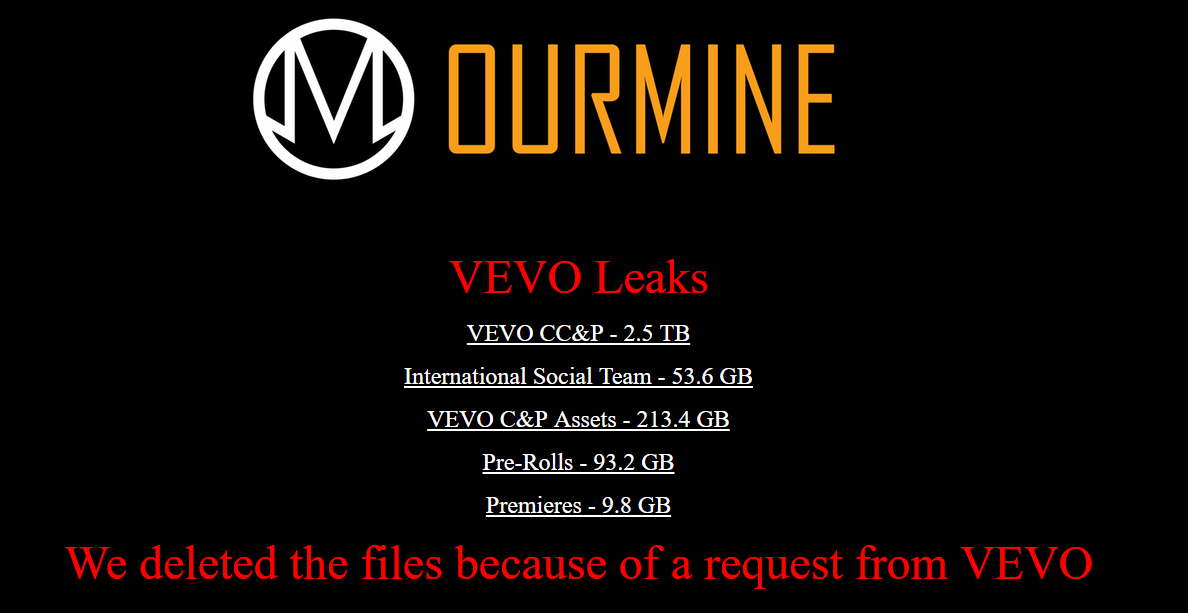
OurMine Group (Saudi Arabian Hacking Group) is now back and has claimed the responsibility for the breach of Vevo which is the most popular online video streaming service. Even Vevo.com is now not…
Read more
Q201. What two words should be avoided as link labels on a web page? Answer – “Click here” should be avoided as link labels on a web page. Q202. Fill in the blank:…
Read more
Previously we exploited a SQL injection vulnerable website with one of the most popular automated tool called as SQLMAP and now in this article, we’ll try to exploit the similar vulnerable website manually…
Read more
Weak or home-grown algorithms A common mistake developers make is to use weak or flawed encryption/hashing algorithms. For example, many developers use md5 or sha1 as their hashing algorithm of choice. Using a…
Read more
A bug bounty program is a deal offered by many websites and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to exploits and vulnerabilities. And…
Read more
WP-Grab-Info is an open source tool through which you can easily detect the WordPress Version, Username, Theme Name and Plugins List. Install WP-Grab-Info in Kali Linux – To install this above said tool,…
Read more