Mozilla has fixed a critical flaw i.e. Remote Code Execution that could allow an attacker to execute arbitrary code on any targeted device. This loophole is due to insufficient sanitization of HTML fragments…
Read more
WordPress is one of the most popular open source blogging platform, with global and vibrant user, developer, and support communities. Though it can be compared to TypePad, Moveable Type, Google’s Blogger(Blogspot), and the…
Read more
We assume most of you know what a Man in the Middle (MitM) attack is, but below is a diagram of a Man in the Middle attack. A man-in-the-middle attack is a…
Read more
With Apponfly, you can get free Windows RDP for full one month and the best thing is that you don’t need any credit card for verification etc. AppOnFly is your secure remote desktop for…
Read more
The best way to put your Wifi adapter to monitor mode is through airmon-ng but with airmon-ng package you can only create a single monitor mode. In this article, you’ll learn how to…
Read more
On October 5, 1991, Linus Benedict Torvalds, a graduate student from the University of Helsinki in Finland, announced in a Usenet newsgroup that he had created a small UNIX-like operating system called Linux….
Read more
Alright, far too often (especially in the IRC channels) there is a time where even the most beginner of users are faced with the terminal. It has many names: terminal, shell, console, “command…
Read more
In this article, we’ll cover two methods through which you can easily test your website loading speed and some other performance factors like Lookup Time, Connect Time, Pre-Transfer Time and Start-Transfer Time. To…
Read more
Kali Linux is the most recent live disk security distribution released by Offensive Security. The latest version i.e. Kali Linux 2017.3 has over 600 security and penetration testing tools included, categorized into helpful groups most…
Read more
Static program analysis is the analysis of computer software that is performed without actually executing programs. In most cases the analysis is performed on some version of the source code, and in the…
Read more
According to the reports, approx 14% of the BTC and ETHER supply have been compromised by the hackers in less than a decade, said by Lex Sokolin, Director of Autonomous Research LLP. When…
Read more
So OnePlus has finally admits that more than 40,000 user’s credit card details have been breached and used in multiple fraudulent transactions who made purchases on its official website in the period of…
Read more
As we’ve discussed earlier, that how we actually deauthenticate a wireless device with the help of aircrack-ng tool suite package by flooding a network with deauthenticate packets. To deauthenticate any wireless device/router/client, its…
Read more
As you all knows profile creation sites are very very useful to create backlinks which actually increase your domain authority rank and results large number of traffic to your website. Getting backlinks for…
Read more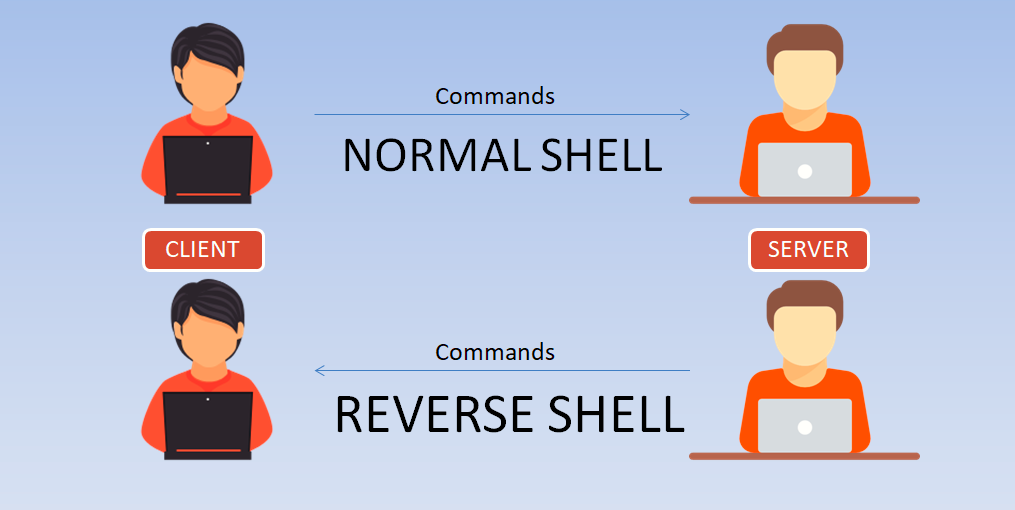
Today we’re are going to show you how to make a reverse shell of any Linux machine. Here in this scenario, we are using two linux based VMs, One is Kali Linux(2017.2) and…
Read more
For decompiling an android application, the open source tool which we’ll use is “dex2jar“. Download Link – Dex2jar.zip (Extract in any location) Sample Application – yeahhub.apk (Download & Extract/Move into dex2jar folder) About…
Read more