
These days, wireless networks are everywhere. With users being on the go like never before, having to remain stationary because of having to plug into an Ethernet cable to gain Internet access is not feasible. For this convenience, there is a price to be paid; wireless connections are not as secure as Ethernet connections. In this tutorial, we will explore a new method for cracking WPA/WPA2 networks with an open source python script wifibroot.
Also Read: Crack WPA2-PSK with Aircrack (Dictionary Method)
WifiBroot is an extensive tool which helps you to crack WPA and WPA2-PSK based wireless networks and is still under development.
Features of WifiBroot –
- Easy to crack WPA and WPA2 Wireless Networks
- Built-in Wireless Sniffer
- Native Packet Manipulation
- Supports Verbose mode (–verbose)
- Store Handshakes in a separate directory (No need to capture again and again for same network)
- Auto-detect EAPOL and Auto-dissociation frames
- Client sorting according to reported power
Installation of WifiBroot –
You can WifiBroot tool with the help of git by typing the following command:
Command: git clone https://github.com/hash3liZer/WiFiBroot
WiFiBroot heavily depends on scapy. So, you would need scapy installed. Almost, every other library would likely be installed on your system. To install scapy, you can use the following command:
Command: sudo pip install scapy
Before to run WifiBroot, make sure that your wireless interface(wlan0) must be in Monitor Mode(wlan0mon) which you can easily done with airmon-ng start <wireless interface> command. So in our case, it is wlan0mon which we’ll use in further commands.
To run wifibroot, type the following command:
Command: python wifibroot.py -i wlan0mon –verbose -d /usr/share/wordlists/rockyou.txt
Here,
- -i defines for wireless monitor interface,
- -d defines for dictionary file path,
- –verbose for verbose output which prints hash values too at the end.
For more info, you can directly type “python wifibroot –help”

If in case, you didn’t mention any dictionary file path then this tool has its own in-built dictionary file located at /dicts/list.txt which works under normal mode.
So this tool will automatically scan all the nearby wireless networks and print all the required information like ESSID (Name of the wireless network), BSSID (Mac Address of the wireless network), Channel No (1 to 13), Encryption Type (WEP, WPA or WPA2) and PWR (In dbm) value.
Based on your choice, (Press CTRL+C to stop the monitoring), and simply select the wireless network from the list which you want to crack as shown below:
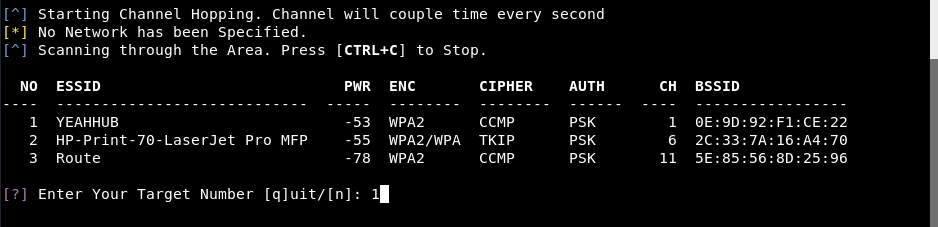
So here, we selected (1) whose ESSID is “YEAHHUB” and BSSID is “0E:9D:92:F1:CE:22”.
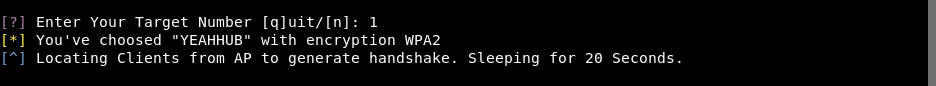
After that, it will automatically searches for all connected clients for handshake generation and the script will listen for default 20 seconds which you can further set the timeout option for listening on the clients with -t <value>.
And the best thing about WifiBroot is that, the script will automatically arrange all the connected clients based on the range reported by the interface which actually increase the chances of generating handshake in less time.
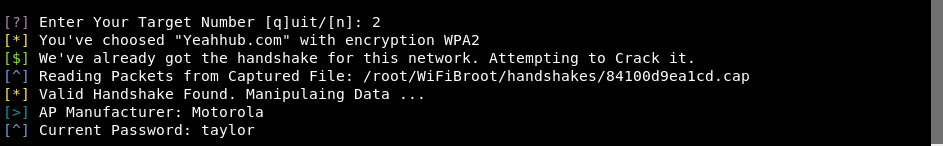
For research facilities, verbose mode will show you live packets as soon as they get captured and will print hexdump of computed hashes. The hashes will include, PMK (Pairwise Master Key), PTK (Pairwise Transient Key) and MIC (Message Integrity Code).
To Crack the password, there is a built-in dictionary in the folder dicts (as already discussed) which contain some of the most dumb passwords. In extension to that, wifibroot also check for default passwords which increase it’s credibility of finding the right hash.
At this stage, you can provide your own dictionary or pass a comma separated string to -p argument like -p “password1,password2,password3”.
Look at the below screenshot:
As soon as it identifies all connected clients, it will automatically send the deauth signal to all clients one by one until it generates the successful handshake. After successful handshake generation, the script will automatically tries to bruteforce based on the dictionary value (provided in 1st step) and gets you the password in clear text manner along with some computed Hash values(PMK, KCK and MIC) as shown below:

All the handshakes for particular wireless network will be stored in a separate directory which will eliminate the requirement for handshake generation for future attempts as shown below:
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times








