
According to the reports, approx 14% of the BTC and ETHER supply have been compromised by the hackers in less than a decade, said by Lex Sokolin, Director of Autonomous Research LLP. When…
Read more
So OnePlus has finally admits that more than 40,000 user’s credit card details have been breached and used in multiple fraudulent transactions who made purchases on its official website in the period of…
Read more
As we’ve discussed earlier, that how we actually deauthenticate a wireless device with the help of aircrack-ng tool suite package by flooding a network with deauthenticate packets. To deauthenticate any wireless device/router/client, its…
Read more
As you all knows profile creation sites are very very useful to create backlinks which actually increase your domain authority rank and results large number of traffic to your website. Getting backlinks for…
Read more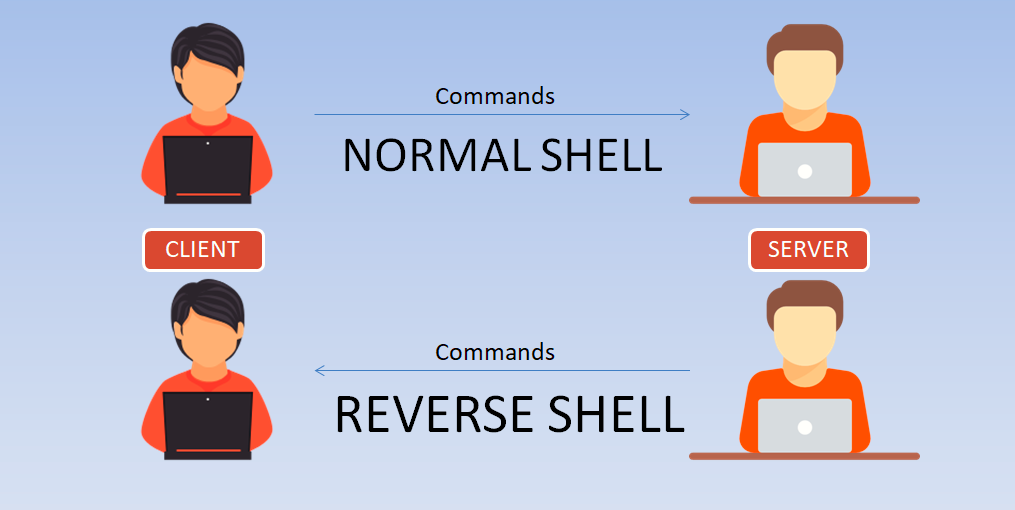
Today we’re are going to show you how to make a reverse shell of any Linux machine. Here in this scenario, we are using two linux based VMs, One is Kali Linux(2017.2) and…
Read more
For decompiling an android application, the open source tool which we’ll use is “dex2jar“. Download Link – Dex2jar.zip (Extract in any location) Sample Application – yeahhub.apk (Download & Extract/Move into dex2jar folder) About…
Read more
1. Autospy Autopsy is a digital forensics platform and graphical interface to The Sleuth Kit and other digital forensics tools. It can be used by law enforcement, military, and corporate examiners to investigate…
Read more
Anyone can, with the right equipment, access wireless networks (wireless local area networks, wlan’s). After all, there is no physical barrier that makes break-in attempts more difficult, as is the case with wired…
Read more
Reverse-engineering is especially important with computer hardware and software. Programs are written in a language, say C, C++ or Java, that’s understandable by other programmers. But to run on a computer, they have…
Read more
For those who are interested in learning how to do Penetration Testing, there are many tools and operating systems are available, but very few targets to practice against safely – not to mention…
Read more
Network scanning refers to the use of a computer network to gather information regarding computing systems. Network scanning is mainly used for security assessment, system maintenance, and also for performing attacks by hackers….
Read more
1. Common Vulnerabilities and Exposures (CVE) CVE (Common Vulnerability and Exposures) is a list of entries, each containing an identification number, a description, and at least one public reference – for publicly known…
Read more
1. Nudge4j Nudge4j is a tiny piece of Java code to make your Java application accessible to the browser. It’s meant for use during development to provide an environment for experimenting with code…
Read more
A conference is a meeting of people who “confer” about a topic. Conference types include: Convention (meeting), meeting of a, usually large, group of individuals and/or companies in a certain field; Academic conference,…
Read more
1. Practical Malware Analysis: A Hands-On Guide to Dissecting Malicious Software 1st Edition Amazon Buy Link – https://www.amazon.com/Practical-Malware-Analysis-Hands-Dissecting/dp/1593272901 Price – $28.78 (Paperback) & $34.35 (Kindle) Rating – 4.5 out of 5 Nostarch Link – https://nostarch.com/malware…
Read more
Nowhere is the term hacker more misconstrued than in the network security field. This is understandable because the very same tools that network security professionals use to probe the robustness of their own…
Read more
SubBrute is one of the most popular sub-domain brute forcing tool through which we can easily enumerate the best possible sub-domains of any domain along with all DNS records. It is one of…
Read more
WPA/WPA2 vastly improves the security of wireless networks; however, the extra protection comes at the price of added complexity to the protocol. Although WPA was developed with security in mind, it does have its own…
Read more



