Have you ever wanted to learn how to hack? Are you more of a hands on learner, then one that can learn from just reading out of a book? Are you interested in developing secure code by understanding how a hacker will attack your application?
If you answered “yes” to any of these questions, then this site is for you. Since 2005, Enigma Group has been providing its members a legal and safe security resource where they can develop their pen-testing skills on various challenges provided by this site. These challenges cover the exploits listed in the OWASP Top 10 Project and teach members the many other types of exploits that are found in today’s applications; thus, helping them to become better programmers in the mean time. By knowing your enemy, you can defeat your enemy.
The exercises presented in this article are very basic, straightforward examples that are designed for people already intending to get involved in penetration testing or are perhaps already practising the craft.
Make sure that, you must login before to do challenges, otherwise you can’t track your activity.
These first 3 challenges are very basic and just an introduction to web exploitation.
Challenge (Basic 1) – Find the Password
- Level – Super Easy
- Tip – View Source
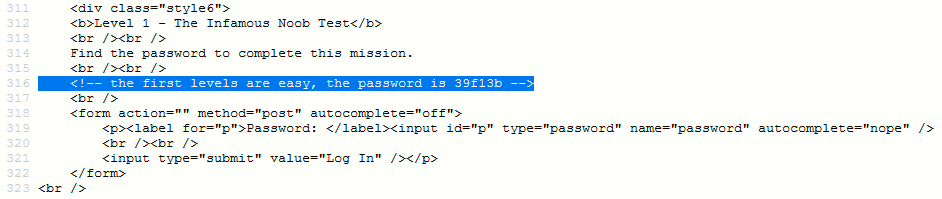
Solution #1 – View the source code to find out the password (Look out the comment field just above the form code). A quick check of the source code reveals the presence of sensitive information like in the following screenshot which reveals the password.
Challenge (Basic 2) – Find out Username and Password
- Level – Easy
- Tip – URL Modification
Solution #2 – Well in this challenge, you need to look out the error which it shows at the top of the form where it shows some absolute path of the site.
By navigating to the /basics/pre/2/dontlookinhere/ directory, following the trail it presents, and going deeper into the directory, you’ll see one secret file named as password.inc which contains your username and password.
Challenge (Basic 3) – Find out Username and Password
- Level – Easy
- Tip – Robots File
Solution #3 – Here you need to find out another username and password. The tip for this challenge is to look out the robots.txt file.
The robots.txt file, also known as the robots exclusion protocol or standard, is a text file that tells web robots (most often search engines) which pages on your site to crawl. It also tells web robots which pages not to crawl. The Robots.txt file is a relevant way of stating hidden pages or data.
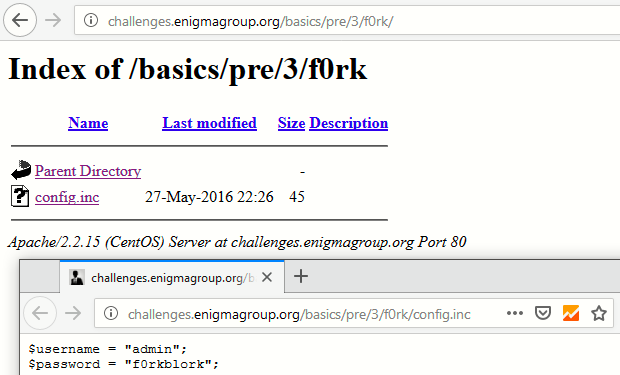
As you can see that, there is a directory named as /f0rk/ which they hide inside robots.txt file.
Let’s navigate to /f0rk/ directory and you’ll see one more interesting file config.inc which contains both username and password.
This is all the info we need to log in and pass the challenge.
Stay tuned for further challenges. Thank You
You may also like:- CTF – Billu B0x – Walkthrough step by step
- Crimemail CTF Writeup – Solution
- CTF – Kioptrix Level 4 – Walkthrough step by step
- CTF – Kioptrix Level 3 – Walkthrough step by step
- CTF – Kioptrix Level 2 – Walkthrough step by step
- CTF – Kioptrix Level 1 – Walkthrough step by step
- CTF – VulnOS2 – Walkthrough step by step
- CTF – Bulldog – Walkthrough step by step