
Before to starting, we’ll setup a virtual pentesting lab with the help of Web For Pentester toolkit which is totally based on Debian OS. As you all knows most of the web applications…
Read more
Well with the help of honeypot, you can easily monitor your own OS and can track every activity of the hacker or you can say that, its the best way to hack the…
Read more
Exploit-DB is one of the most popular platform for their collection of exploits and whitepapers related to Linux/Windows/Assembly/Web/DOS etc. Exploit-DB is the ultimate archive of exploits, shellcode, and security whitepapers. You can easily…
Read more
Q151. Fill in the blank: ____________ tags surround each item in a select menu. Answer – option tags surround each item in a select menu. Q152. True/False: The fieldset tag is used to…
Read more
A web page is composed of multiple features. There are so many SEO tools are also available through which you can also boost your SEO ranking in short manner. Here are the ones…
Read more
Technology advances have significantly changed our lives during the past decade. We rely on computers of various sorts for even the simplest of daily tasks and become stressed when they are not available…
Read more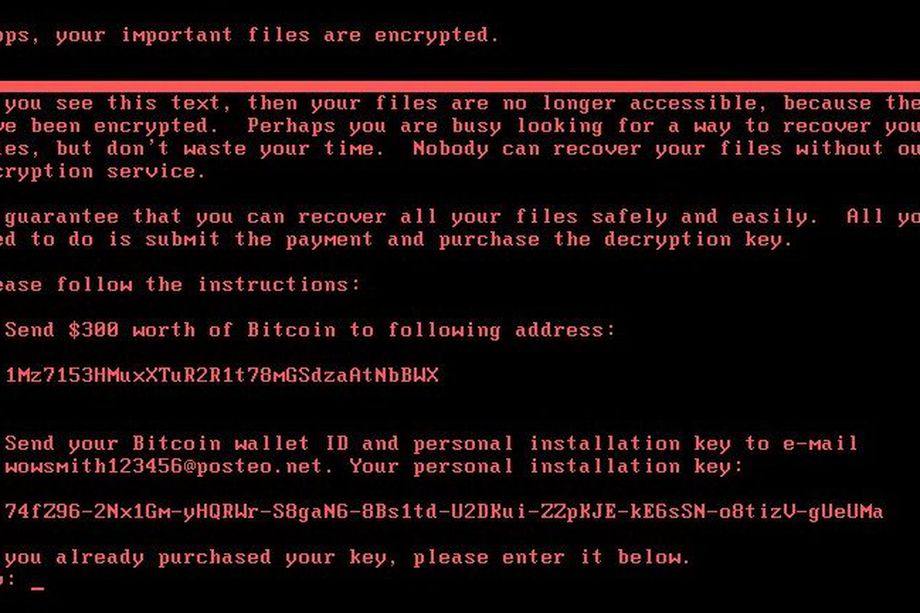
As you all knows, recently Petya Ransomware comes into existence and affected more than 65+ countries. Many organizations in Europe and the US have been affected by this ransomware attack. Although its not…
Read more
As you all knows Wannacry or Wcry Ransomware already created a havoc across the globe and now within the span of just 2 months, a new ransomware named as Petya Ransomware hits globally…
Read more
Today we are introducing a new tool called as “MINIPENGUIN” through which you can easily hack the current user accounts of KALI Linux OS. Mimipenguin is a tool which helps you to dump…
Read more
Q126. True/False: To add a caption to a table, you use the caption attribute in the opening table tag. Answer – False. Q127. If you include a thead or a tfoot group in…
Read more
Whether you want to start a website for fun or to make money, you’ll first have to learn how to make a website. Making a website is not difficult at all. In fact…
Read more
Bitcoin is a form of digital currency, created and held electronically. No one controls it. Bitcoins aren’t printed, like dollars or euros – they’re produced by people, and increasingly businesses, running computers all…
Read more
Q101. True/False: A link to a multimedia file is the same as any other link because it also uses the a tag. Answer – True. Q102. What is the purpose of the param…
Read more
To protect your business, an end-to-end security strategy that encompasses these many considerations is a must. Defining and communication your board’s information Risk Regime is central to your organization’s overall cyber security strategy….
Read more
An recent ransomware attack that affected more than 100k+ systems on Friday(12th May 2017) has spread to 90+ countries, locking doctors in the U.K. out of patient records at NHS. The attack has…
Read more
Microsoft has provided a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003. And if you are using…
Read more





